Vendor Risk – 10 types you should know

In this fast-paced world, it is now almost impossible for any company to operate without third-party vendors, whether they provide legal assistance, human resource services, payroll services, marketing services, or logistics services.
On the contrary, vendors with access to your network and company data can pose a threat to your business. Thus, it has become imperative for companies to implement a Vendor Risk Management program to stay safeguarded from compliance, and operational and reputational risks.
Why do you need to manage your vendor risks?
Companies face risks when they engage in third-party services. Working with vendors who handle confidential, sensitive, proprietary, or classified information is especially risky. Even if your internal security measures are strong, third-party vendors who do not follow best practices can be a big threat.
What is vendor risk management?
An organization’s third-party risk management program is one of the most important components of its information security program. In today’s business environment, companies are dealing with more vendors who have access to company-sensitive data and sometimes confidential information, and this number is growing rapidly.
As a result, your organization can be more susceptible to experiencing an information security incident if you fail to properly understand and manage these risks.
Why it is important to manage your vendor risks?
Having a solid understanding of vendor or third-party risk management will help your business avoid unacceptable risks and protect its reputation.
The role of VRM is to manage and monitor the risks associated with third-party vendors and suppliers. A vendor risk assessment should be carried out once you identify potential third-party vendors to supply goods or services.
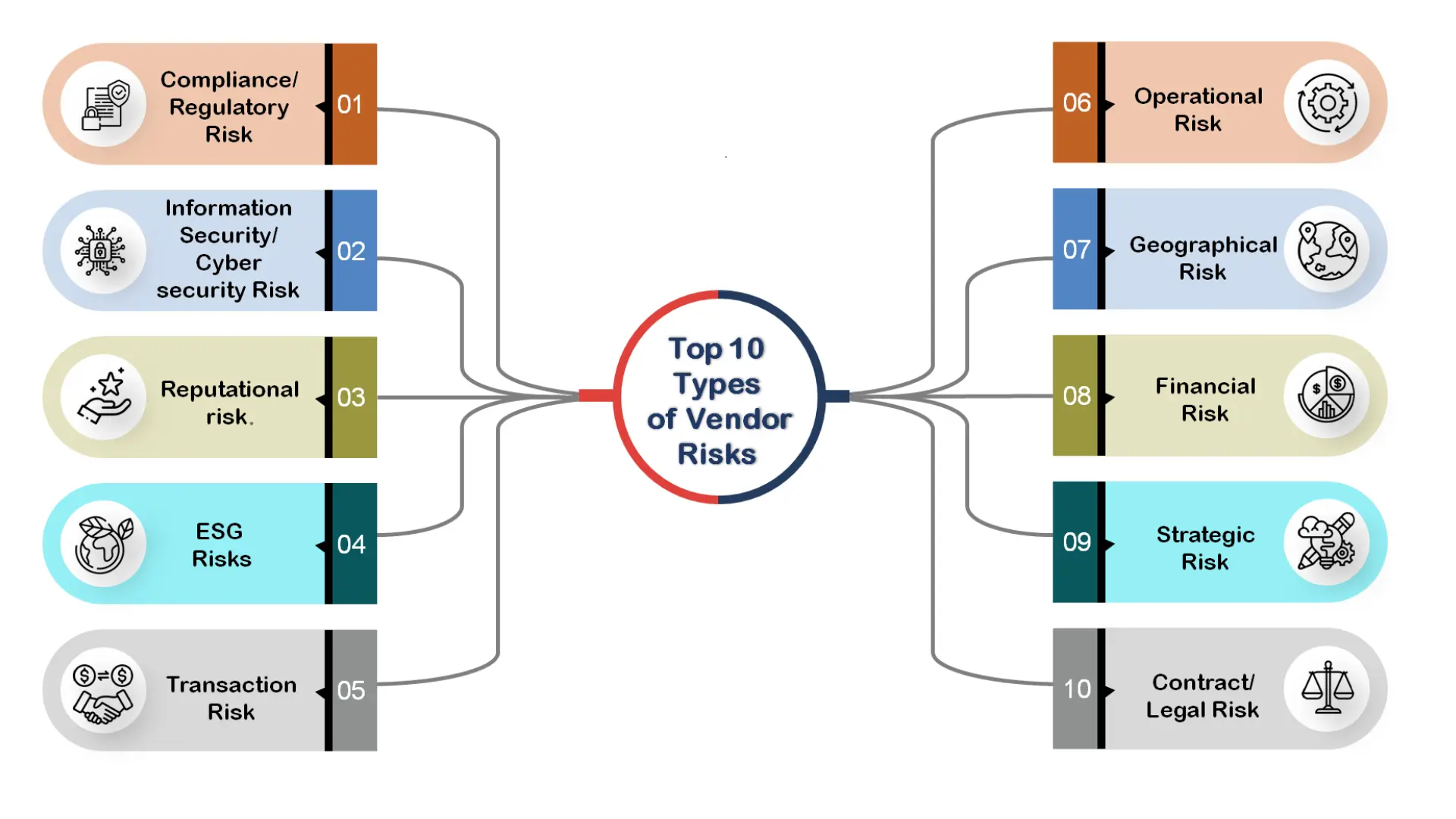
Types of Vendor Risks for Companies to Monitor
10 types of risk management every company deals with when managing vendor relationships:
1. Compliance/Regulatory Risk
Compliance or regulatory risk arises when third-party vendors fail to adhere to contractual, legal, or industry-specific regulations. Vendors must comply with all relevant laws, industry standards, and internal business policies. Non-compliance can result in legal penalties, hefty fines, and reputational damage for your business. Implementing a strong vendor compliance management system helps mitigate risks and ensures regulatory adherence.
2. Information Security/Cybersecurity Risk
Cybersecurity and information security Data breaches, ransomware, and the more frequent cyber occurrences are among the risks. All businesses can be vulnerable to cyber security risks, including major financial institutions, local community banks, healthcare providers, credit unions, energy utilities, producers, and merchants.
Since many firms have shifted to remote work and began depending on unencrypted server access and video conferences, this risk has become even more frequent.
- SaaS (software as a service) and Cloud Risk are comparable to information security risk, but it solely pertains to data that is only available online or digitally. Because many companies are moving away from on-premise data centers to towards cloud storage, cloud risk is a significant new area of third-party risk management. Despite many advantages, including dependable and convenient access, faster delivery, uniformity, and price, security threats started to matter because of:
- Poor security procedures
- Infractions of regulations
- Application security holes
- Infections with malware and data breaches
Similar to when cybercriminals assault a business data center, the outcome is reputational harm, brand tarnishment, and potential income loss.
3. Reputational risk
As previously stated, is a possibility that consumers, the media, investors, and the general public will have a negative perception of your organization.
Numerous factors, including the inability to deliver, a decline in quality, poor customer service, inappropriate workplace practices, and security breaches, can contribute to this dissatisfaction and disrupt your public image.
4. Environmental, social, and governance (ESG) Risks
These risks are related to reputation or brand, legal, technological, compliance, and product or service quality. They also relate to sustainability, such as a vendor’s carbon footprint, how they handle water and wastewater, etc.
Vendors who are irresponsible with the environment and worker safety procedures might put your company at risk for sustainability, non-financial loss, or extra-financial loss.
5. Transaction Risk
Transaction risk arises when vendors fail to deliver the promised goods or services, impacting business operations. If your software or IT vendor cannot maintain servers, hardware, or essential systems, frequent disruptions may occur. Businesses must assess vendor reliability and long-term partnerships to mitigate risks and ensure seamless operations.
6. Operational Risk
Operational risk stems from ineffective internal systems, faulty processes, or human errors, affecting business continuity. External factors like vendor failures can further amplify risks, leading to workflow disruptions and production halts. Companies should implement robust risk management strategies to safeguard operations and minimize potential losses.
7. Geographical Risk
Geographic risk is when the location of your suppliers has an effect on your company. When doing business with overseas vendors, one must adhere to international standards and laws. For those who do business with European companies, the General Data Protection Regulation (GDPR) and its safeguards for privacy and data have become a major worry.
- Geographic concentration risk is when a company relies too heavily on a single provider or set of vendors in a certain area. You put yourself at risk for the effects of natural disasters, pandemic breakouts, and political unrest in that region if you outsource to one vendor for several important business services or to several vendors close to one another who employ the same third-party vendors.
8. Financial Risk
Financial risk is the potential for a vendor connection to have a negative financial impact on your company.
If a supplier or subcontractor delivers subpar goods or services, your business risks failing to meet fiscal-year or production limits. When an organization’s financial performance suffers, it may be more difficult to pay off debt or provide value to shareholders.
- Credit risk is the possibility that a business’s financial stability or capacity to control debt would negatively impact operations. Avoid doing business with a seller who has a track record of making poor financial judgments and has a low credit score.
9. Strategic Risk
Negative business decisions or a lack of compliance with established corporate procedures and strategic objectives directly cause strategic risk. Rapidly changing business and market trends, technology advancements like the Internet of Things (IoT) and Big Data, and a quick reevaluation of workplace best practices because of COVID-19 have all contributed to the urgency of strategic risks.
10. Contract/Legal Risk
These risks occur when a prerequisite is not satisfied, a deadline is not reached, contracts are handled differently by different departments, or an automatic rollover clause is overlooked. A vendor’s compliance with the terms and conditions of a contract that your legal department drafted may be essential to your business’s operation. In contrast, a seller may smuggle ambiguous language and provisions into their contracts.
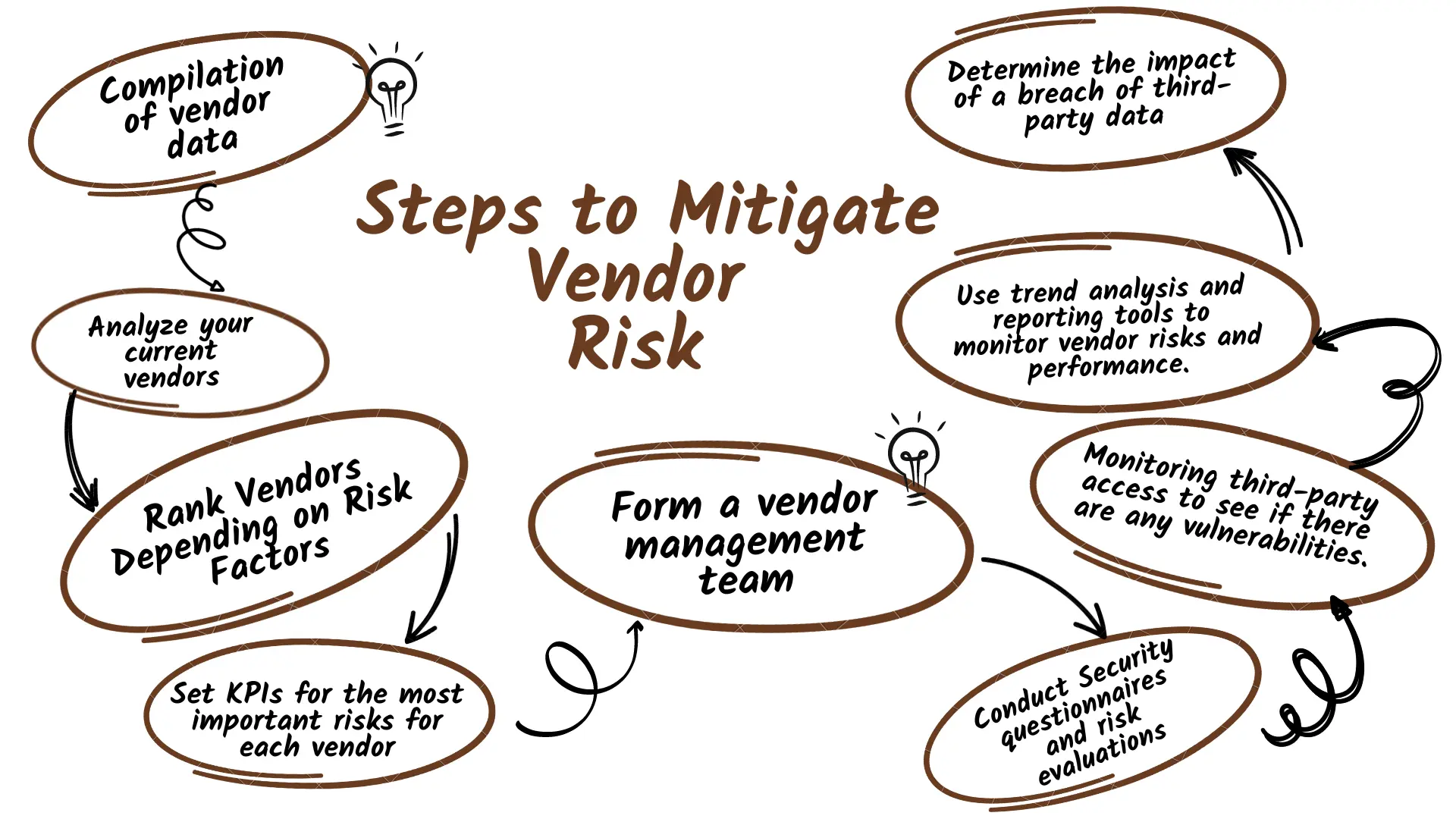
How to mitigate vendor risks?
The different risks posed by third parties should be identified, and procedures should be put in place to monitor and minimize the vendor risks you are most concerned about.
Step 1: Compilation of vendor data
Technology enables the mapping of the vendor hierarchy and the integration of vendor data in a single location. This improves visibility into vendor profiles and provides a “single source of truth” for vendors.
Step 2: Analyze your current vendors
Identifying which of your vendors is most essential to your operations is a crucial step in controlling vendor risk. You should also consider the level of access that each of your vendors requires in order to effectively carry out its functions.
Step 3: Rank Vendors Depending on Risk
Think about which of your providers presents the greatest danger. The tiers that are most frequently used are:
- Tier 3 suppliers: Low criticality and risk
- Tier 2 suppliers: Medium criticality, medium risk
- Tier 1 suppliers: High criticality and risk: Vendors classified as high-risk should be closely watched and controlled more so than those classified as low-risk.
Step 4: Set KPIs for the most important risks for each vendor
Construct solid vendor agreements that specify the criteria your business can use to exit a relationship if KPIs are not reached.
Step 5: Form a vendor management team (VMT)
Members of this group may come from several departments inside your business, including IT, legal, compliance, and privacy. The VMT can assist you in identifying the suppliers who pose the highest risk to your business and in creating mitigation plans to guard against them.
Step 6: Conduct Security questionnaires and risk evaluations
Vendor questionnaires and threat intelligence are used in third-party risk assessments to help businesses estimate the level of risk that particular providers pose. Commonly used standards for evaluating businesses include:
- ISO 27001
- ISO 27701
- NIST SP 800-53
- SIG Lite and SIG Core
- CSA CAIQ
Step 7: Monitor to see any vulnerabilities by keeping track of the what, when, and how of third-party access
This will allow you to fix them right away. Although this may seem complicated, flexible automation of these procedures will help you save time and money, improve your workflow, and keep your company safe.
Step 8: Tools for trend analysis and reporting make it easier to monitor vendor risk and performance
By combining data from diverse business processes, related vendor connections, and risk management frameworks, businesses can make better business decisions. The outcomes are then examined in light of all vendor governance programs.
Step 9: Determine the impact of a breach of third-party data.
Public relations and legal considerations should both be made in this. What harm might result from the unauthorized exposure of your private information? Who would be responsible should the vendor be breached, either due to negligence or malice? What measures must your company take to ensure that leaks never happen?
What to do if a vendor risk occurs?
No company ever wants to learn that one of its suppliers has the potential to pose a threat to the company. Still, if it happens, then there are seven critical ways to follow that can minimize threat and reputational damage.
- Communicate with your clients. Trying to cover up the breach could indeed do more damage to your reputation.
- Notify controllers and law enforcement. Ensure that all laws and regulations about data breach announcements are followed.
- Examine the breach. How and where did it happen, and how numerous records were affected?
- Offer protection to customers. Any breach that involves client data also raises the threat of identity theft. Credit monitoring services can help rebuild client trust.
- Secure and tighten network security. Did the breach reach your company via a seller’s system? If it did, take essential steps to correct the flaws in your own security.
- Ensure that your vendors protect client data. Now is the time to establish a schedule for ongoing checks, If you’re not checking this regularly. Review the relationship with any seller that’s unintentional to share in this process.
- Apply a vendor risk management plan. Implement this plan for all existing vendors and use it to evaluate new suppliers as well.
Why SignalX for your Vendor Risk Management?
Our comprehensive solution streamlines and automates your vendor due diligence workflow from beginning to end. Our 26-parameter vendor risk scorecard and risk rating solution give you a 360-degree view of the onboarding process.
In the world of AI and automation, with SignalX’s vendor risk management solution, you can ensure that your company always stays compliant with the regulations, reduce vendor onboarding TAT, and most importantly keep a regular eye on the risk factors and mitigate them early on.
Want to improve your vendor due diligence process and shield your business from risks? Book a meeting with us to find out how we can make that happen for your use case.



