What Is Compliance Monitoring? Definition, Examples & Best Practices

Compliance monitoring is a crucial part of maintaining the integrity of your organization, ensuring that policies, regulations, and standards are followed. It’s no longer enough to conduct a one-time audit or compliance review. With increasing regulatory demands and the fast-paced nature of business, continuous monitoring has become a necessity. This approach provides real-time visibility into your organization’s compliance status, helping to identify risks before they escalate.
In this article, you’ll learn the basics of compliance monitoring, its importance, various tools available, best practices, and how to implement an effective program that keeps your organization safe from risks like fines, data breaches, and reputational damage.
What Is Compliance Monitoring?
Definition of Compliance Monitoring
Compliance monitoring refers to the ongoing process of tracking and verifying an organization’s adherence to internal policies, external regulations, and industry standards. Unlike audits, which are typically periodic, compliance monitoring is designed to continuously check if a business is operating in accordance with rules and regulations.
It involves reviewing processes, systems, and activities on a consistent basis, helping organizations mitigate risks and maintain compliance over time.
Compliance Monitoring vs. Audits & Compliance Programs
While both audits and compliance programs aim to ensure adherence to standards, compliance monitoring focuses on real-time oversight. Audits are typically one-time or periodic checks, whereas monitoring is continuous, making it more proactive. A compliance program is broader in scope and includes strategies, policies, and training monitoring is one aspect of this program, focused on execution and tracking.
Common Compliance Domains
Compliance monitoring spans multiple industries and regulatory domains. Some of the most common include:
- Financial Services: Ensuring adherence to regulations like the Sarbanes-Oxley Act, Dodd-Frank, and the Basel Accords.
- Healthcare: Monitoring compliance with regulations such as HIPAA and Medicare.
- Data Privacy: Ensuring that personal data is protected according to GDPR, CCPA, or other privacy laws.
- Cybersecurity: Monitoring for compliance with standards like NIST, ISO/IEC 27001, and the Cybersecurity Maturity Model Certification (CMMC).
Why Compliance Monitoring Matters
Risk Reduction
Non-compliance can lead to significant financial penalties, legal consequences, and reputational harm. A proactive monitoring program helps identify and mitigate compliance gaps before they result in costly fines or legal challenges.
Operational Benefits
Continuous monitoring enables early detection of potential issues, allowing for swift action to correct them. Additionally, it fosters a culture of continuous improvement, making it easier for organizations to stay ahead of regulatory changes.
Business Outcomes
A well-established compliance monitoring system builds stronger internal controls, which enhance stakeholder trust and confidence. By demonstrating that compliance is a priority, organizations improve their reputation with clients, customers, and investors.
Types & Approaches to Compliance Monitoring
Manual vs. Automated/Continuous Monitoring
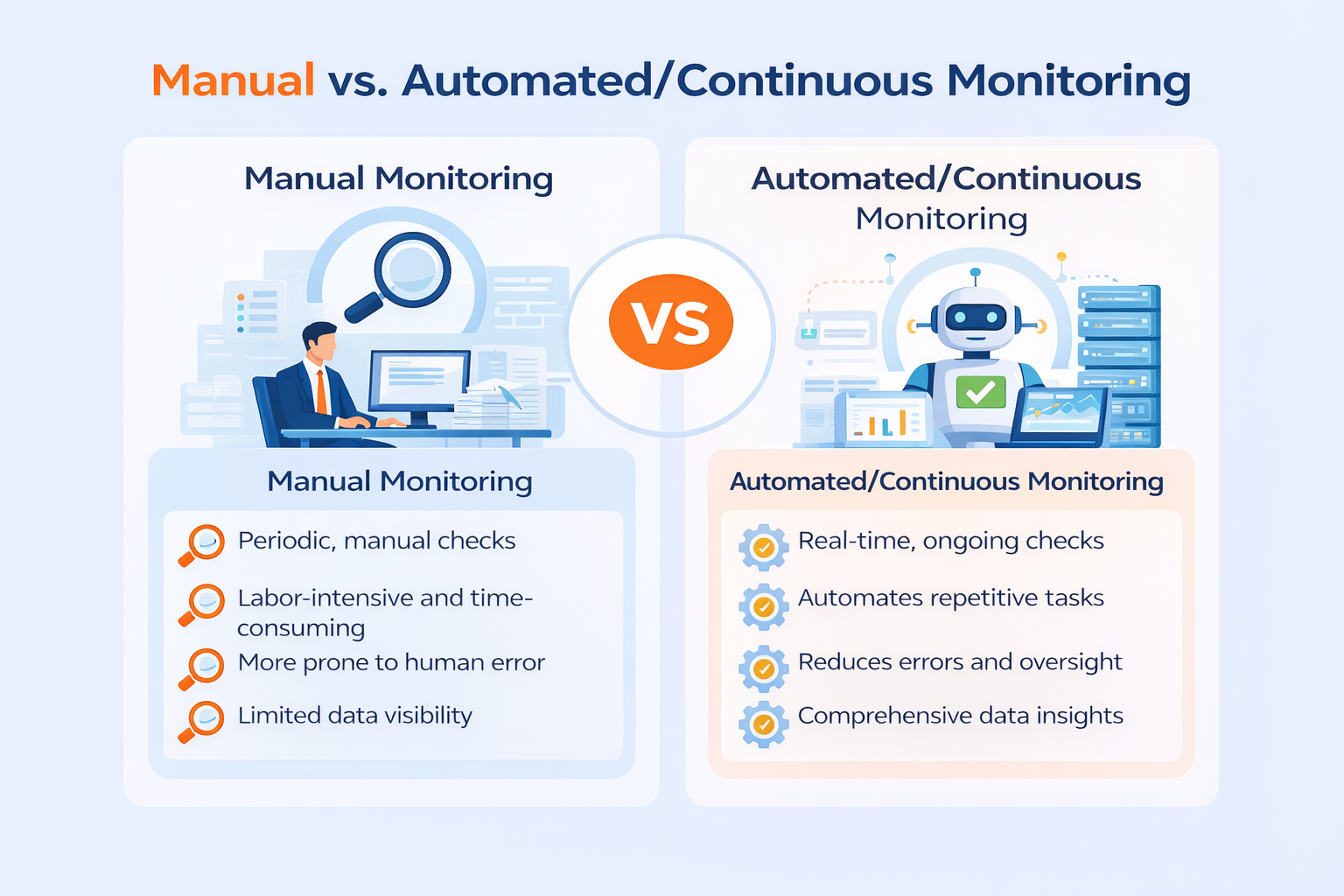
Manual Monitoring: Traditionally, organizations have relied on manual checks and periodic audits to ensure compliance. However, this approach can be time-consuming, prone to human error, and not well-suited to the complexity and speed of modern regulatory environments.
Automated/Continuous Monitoring: In contrast, continuous monitoring automates the collection and analysis of compliance data, providing real-time insights into potential risks and gaps. This approach is more efficient, scalable, and helps identify issues as they arise.
Detective, Preventive, and Corrective Controls
- Detective Controls: These identify and detect compliance violations after they have occurred (e.g., system alerts for unauthorized access).
- Preventive Controls: These are designed to prevent compliance violations before they occur (e.g., role-based access control).
- Corrective Controls: These involve actions taken to correct a compliance breach once detected (e.g., patching security vulnerabilities).
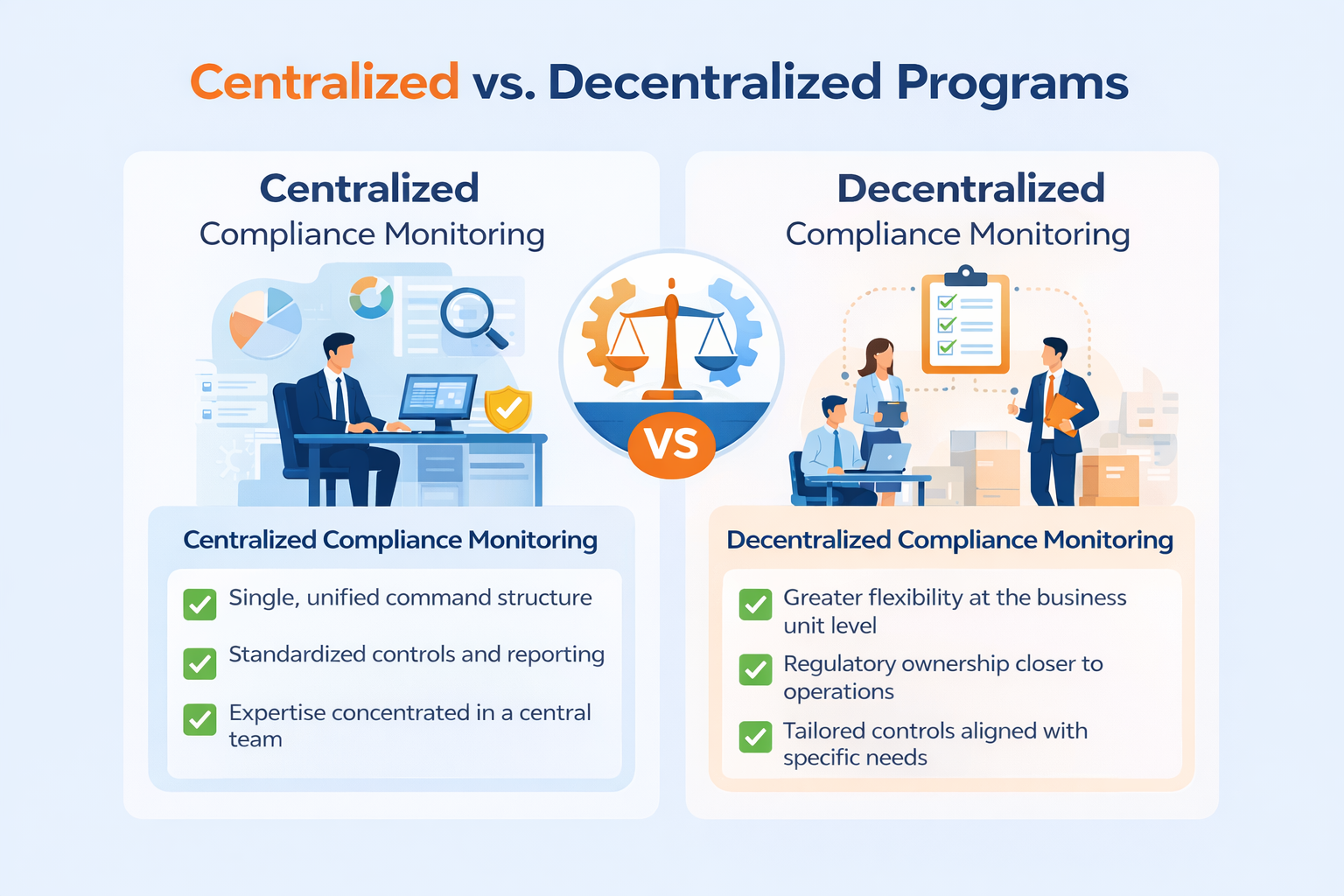
Centralized vs. Decentralized Programs
A centralized compliance program involves a single, unified approach to monitoring across the entire organization. It can be easier to manage but may lack flexibility. A decentralized program, on the other hand, places responsibility for compliance monitoring with individual business units or departments, allowing for more tailored approaches but potentially creating challenges in coordination.
Core Components of an Effective Compliance Monitoring Program
Governance & Ownership
A clear governance structure ensures accountability for compliance. Typically, the compliance officer is responsible for overseeing the program, but ownership often extends to department heads, legal teams, and IT personnel. Everyone should be aligned on roles and responsibilities.
Regulatory Mapping & Control Design
Mapping regulations to specific controls is critical for maintaining compliance. This step involves identifying the relevant laws and designing processes and policies that ensure those regulations are met.
Data Collection & Evidence Management
An effective program must have mechanisms in place for collecting data and maintaining evidence of compliance. This includes securing logs, audit trails, and transaction histories, which will be crucial during audits or investigations.
Monitoring Cadence and KPIs
Determining how often compliance checks will occur is key to ensuring ongoing compliance. Key performance indicators (KPIs) such as the percentage of controls tested or the time to remediate issues are essential for tracking the effectiveness of the program.
Issue Remediation Workflows and Escalation Paths
When violations or risks are identified, it’s crucial to have a defined process for remediation. This includes setting up workflows for addressing the issue and escalation paths for when issues require higher-level intervention.
Technology Integration
Leveraging technology such as Security Information and Event Management (SIEM), Governance, Risk, and Compliance (GRC) platforms, and RegTech tools helps automate monitoring and improve the speed and accuracy of compliance checks.
Compliance Monitoring Tools & Technology
Compliance monitoring tools vary depending on the organization’s needs and the industry in which it operates. Some popular types of tools include:
- GRC Platforms: These help manage risk, policies, and compliance in an integrated system.
- Continuous Monitoring/Security Posture Tools: These provide real-time tracking of compliance with security controls.
- Communication Surveillance Tools: For industries like finance, tools that monitor communications (emails, phone calls) for compliance are essential.
- Automated Evidence Collection Tools: These simplify the process of gathering and storing evidence for audits or compliance verification.
Choosing the Right Tools
When selecting tools, consider factors like scalability, ease of integration with existing systems, reporting capabilities, and audit trails. It’s important to choose a tool that can grow with your organization’s compliance needs.
Step-by-Step: How to Start a Compliance Monitoring Program
Quick-Start Checklist
- Identify Relevant Regulations: Understand the laws and standards that apply to your business.
- Map Controls to Regulations: Design policies and procedures to meet the identified requirements.
- Select KPIs: Choose measurable metrics to track compliance and performance.
- Choose the Right Tools: Select the tools that best align with your needs.
- Pilot the Program: Start with a small-scale pilot to test the system.
- Scale the Program: Once successful, expand the program to cover all areas of the organization.
Pilot Tips & Common Pitfalls
Pitfalls: Don’t overlook small compliance areas, as they can lead to bigger issues. Additionally, don’t rush the testing phase ensure everything works as expected before scaling.
Pilot Tips: Begin with a focused scope (e.g., one department or regulatory area), gather feedback, and adjust the approach before going organization-wide.
Real-World Examples & Use Cases
Financial Services: Communication Archiving
In the financial sector, organizations must comply with regulations like FINRA and SEC rules. One common compliance monitoring practice is archiving communication data (e.g., emails, chats) to ensure that all financial transactions and advice are properly documented and auditable.
Healthcare: HIPAA Access Logs
Healthcare organizations use compliance monitoring to track who accesses sensitive patient information. Monitoring HIPAA access logs helps prevent unauthorized access and ensures that only approved personnel can view protected health information.
IT Security: Continuous Configuration Monitoring
For IT security, continuous monitoring of system configurations is critical to ensure compliance with cybersecurity standards like ISO 27001. Tools that track configuration changes help identify vulnerabilities and non-compliance in real-time.
Best Practices & Advanced Tips
Continuous Monitoring and Automation: Embrace automated, real-time monitoring to identify issues as they happen.
Risk-Based Prioritization: Focus monitoring efforts on areas with the highest risk.
Evidence Retention & Audit-Readiness: Retain evidence in a secure, accessible format for audit readiness.
Cross-Functional Collaboration: Ensure that compliance monitoring involves collaboration across legal, IT, HR, and other departments.
For a quick start, download our compliance monitoring checklist today!
Common Challenges & How to Overcome Them
Data Silos: Integrate systems to ensure all relevant data is accessible for compliance monitoring.
Alert Fatigue: Use intelligent filtering and prioritization to ensure critical alerts are noticed.
Keeping Up with Regulatory Change: Set up a system for tracking regulatory updates and automatically adjust controls.
Resource Constraints: Consider using automated tools to reduce manual effort.
KPIs & Metrics to Measure Program Effectiveness
% Controls Tested: The percentage of controls that have been tested for compliance.
Mean Time to Remediate: The average time it takes to fix compliance issues.
Incidents Detected: The number of compliance violations detected before they escalate.
Audit Findings Trend: Track whether audit findings improve over time.
FAQ
Is Compliance Monitoring the Same as Auditing?
No, compliance monitoring is ongoing and real-time, while audits are periodic reviews.
How Often Should Monitoring Run?
Continuous monitoring ensures compliance in real-time, while some aspects might be reviewed more frequently based on risk.
What Tools Support Continuous Monitoring?
Tools like SIEM, GRC platforms, and RegTech tools enable continuous compliance monitoring.
Who Owns Compliance Monitoring?
The compliance officer typically oversees the program, but responsibilities often extend across departments.
Conclusion
A strong compliance monitoring program is vital for minimizing risk and maintaining business integrity. The first step is to identify the regulations that apply to your organization and begin mapping controls. From there, pilot a monitoring solution to ensure you’re ready for the challenges of continuous compliance.
For a quick start, download our compliance monitoring checklist today!
