Third-Party Risk Management Lifecycle: A Strategic Approach

The functioning of modern businesses depends heavily on partnerships with third parties. Organizations depend on outside suppliers, service providers, and vendors to assist them in reaching their objectives and satisfying clientele.
However, in order to secure the company’s assets, data, and reputation, risks associated with these connections must be identified, evaluated and mitigated.
Identifying, evaluating, and controlling risks that result from third-party connections is the process of managing third-party risk. Third-party partnerships are a frequent entry point for cyber attackers, data breaches, and other security issues.
Therefore this is an essential aspect of any risk management programme. The identification and categorization of third-party risks, risk assessment and due diligence, risk mitigation and control, contracting and relationship management, incident response and remediation, continuous improvement and risk optimization are some of the stages that make up the third-party risk management lifecycle.
Stage 1: Identification and Categorization of Third-Party Risk
The first stage in controlling third-party risk management lifecycle is the identification and categorization of third-party relationships. It entails identifying and classifying every third-party provider that a company works with, determining the amount of risk attached to each provider, and allocating resources for risk management in accordance with the results.
Best practices for identifying third-party providers:
An organization should do a thorough inventory of all the vendors, suppliers, contractors, partners, and other third-party providers it engages with in order to identify all of them. Information like the services offered, the nature of the connection, and the degree of access to private information or systems should all be included in this inventory.
Other recommended practices for finding third-party suppliers include reviewing the inventory frequently to make sure it is complete and up to date as well as employing automation technologies to speed up the identification procedure.
Factors to consider when categorizing third-party providers:
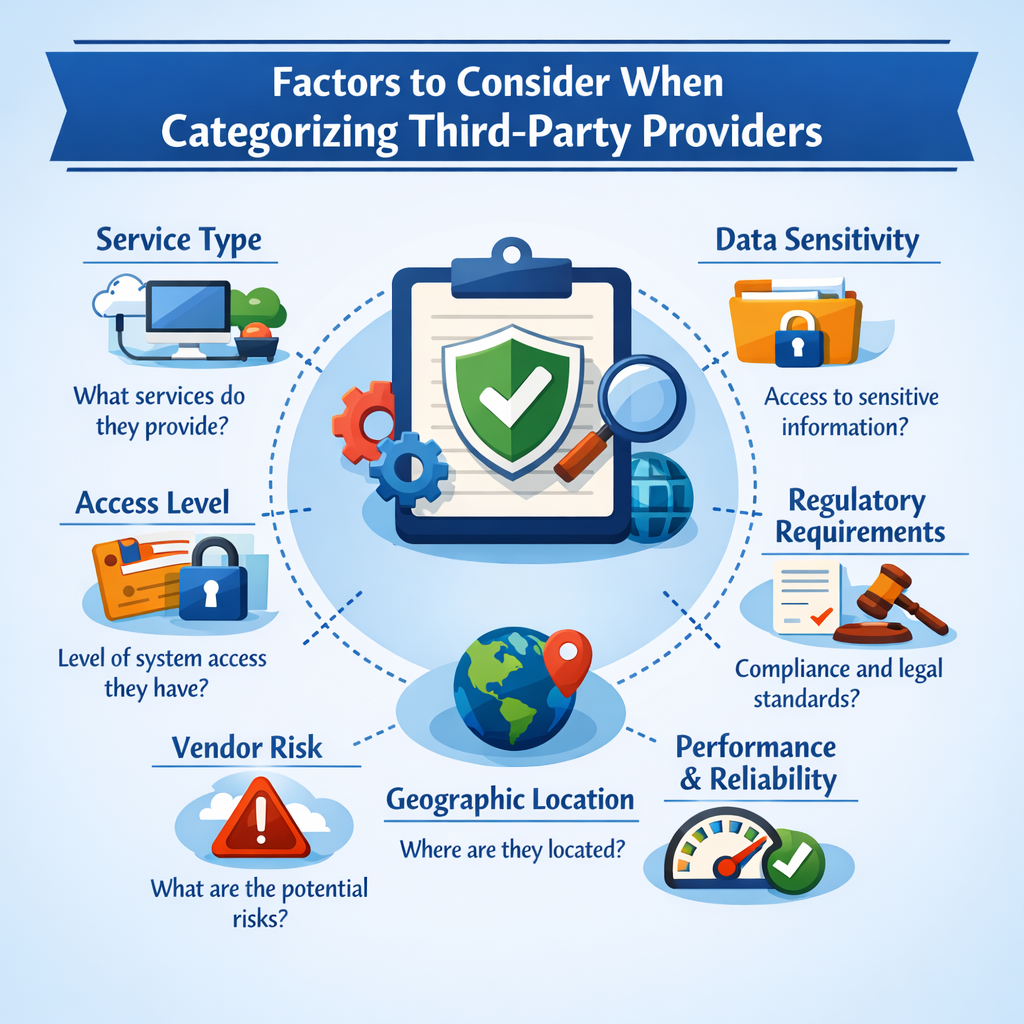
There are several things to take into account when classifying third-party suppliers. These elements consist of the following:
- Level of access to sensitive data or systems: High-risk providers are often those who have extensive access to sensitive data or systems.
- Relationship type: In general, higher-risk providers are those who play a more crucial part in the organization’s operations.
- The industry or sector: Some industries or sectors could be more vulnerable to specific hazards, such as fraud or data breaches.
- Regulatory compliance: Providers that must comply with regulations may run a higher risk and should be categorized as such.
- Financial stability: Organizations may be more at risk from providers who are in financial instability.
Stage 2: Risk Assessment and Due Diligence
The second stage of the TPRM lifecycle involves assessing risks associated with third-party providers and conducting due diligence to ensure their credibility and reliability.
Key Steps in Risk Assessment
- Identify Potential Risks: Evaluate threats related to financial stability, business continuity, regulatory compliance, and data security.
- Analyze Likelihood and Impact: Assess the probability and consequences of identified risks.
- Classify Third-Party Risk Levels: Differentiate between low, medium, and high-risk third parties to allocate risk management efforts effectively.
Best Practices for Due Diligence
- Verify Provided Information: Assess financial data, legal documents, security policies, and business history.
- Conduct On-Site Visits and Interviews: Engage key personnel to validate security practices and operational processes.
- Implement Tiered Due Diligence: Apply varying levels of scrutiny based on the risk profile of each third-party provider.
Ongoing Risk Monitoring and Compliance
- Set Security Guidelines: Establish strict security policies, including data encryption, access controls, and regulatory compliance measures.
- Regular Audits and Assessments: Conduct periodic reviews of third-party security practices and risk levels.
- Continuous Reporting and Monitoring: Require frequent security reports and risk assessments to ensure ongoing compliance.
By following these best practices, organizations can enhance their Third-Party Risk Management (TPRM) strategies, ensuring stronger compliance, security, and operational resilience.
Stage 3: Risk Mitigation and Control
Once risks are identified, organizations must implement strategies to mitigate and control them effectively.
Risk Mitigation and Control Strategies
- Contractual Clauses: Businesses should include specific contractual clauses addressing data security, privacy, regulatory compliance, and indemnity.
- Continuous Oversight: Implement regular monitoring of third-party activities, access levels, and compliance.
- Data Protection Measures: Use access restrictions, encryption, and regular backups to secure sensitive data.
- Incident Response Protocols: Define clear procedures for responding to security breaches, stakeholder notifications, and remediation.
- Risk Transfer Mechanisms: Leverage insurance and indemnity agreements to reduce financial exposure.
Monitor risks in real-time, prioritise threats, and make smarter, data-driven decisions.
Stage 4: Contracting and Relationship Management
Organizations must establish structured contract negotiations and relationship management to ensure risk mitigation.
Key Components
- Negotiating and Drafting Contracts: Define service expectations, pricing, performance standards, and liability clauses.
- Service Level Agreements (SLAs): Set performance benchmarks, response times, and resolution timeframes.
- Relationship Management: Establish dedicated teams to monitor third-party performance and compliance.
- Contractual Compliance: Conduct regular audits to ensure third parties adhere to agreed-upon obligations.
- Periodic Contract Reviews: Update SLAs and compliance requirements to align with business needs and regulatory changes.
Stage 5: Incident Response and Remediation
Organizations must have a well-defined incident response plan to handle security breaches and operational disruptions.
Key Steps in Incident Response
- Incident Identification and Containment: Rapidly detect and control security breaches.
- Stakeholder Communication: Notify internal teams, regulators, and impacted parties.
- Remediation Measures: Strengthen security controls, policies, and employee training.
- Post-Incident Evaluation: Conduct root-cause analysis and improve response strategies.
Stage 6: Continuous Improvement and Risk Optimization

A third party risk management lifecycle programme must include constant improvement and risk optimization. Organizations must regularly refine their third-party risk management strategies to stay ahead of evolving threats.
Implementing a Continuous Improvement Framework
A continuous improvement framework is essential for ensuring that the third-party risk management lifecycle program remains effective and relevant. The following are the key steps in implementing a continuous improvement framework:
- Establish Goals and Objectives: The first step is to establish goals and objectives for the continuous improvement program. These goals and objectives should be aligned with the organization’s overall risk management strategy.
- Define Metrics and KPIs: Once the goals and objectives are established, the next step is to define metrics and key performance indicators (KPIs) to measure the effectiveness of the program. Metrics and KPIs should be specific, measurable, achievable, relevant, and time-bound (SMART).
- Collect Data: Collecting data is critical to identify areas of improvement. Data can be collected from various sources like internal audits, external assessments, and feedback from stakeholders.
- Analyze Data: Analyze the data to identify trends, patterns, and potential risks. This analysis will help to identify areas of improvement and develop strategies to mitigate risks.
- Implement Improvement Strategies: Based on the analysis, develop and implement improvement strategies. These strategies should be designed to address the identified risks and improve the overall effectiveness of the third-party risk management lifecycle program.
- Monitor and Evaluate: Once the improvement strategies are implemented, it is essential to monitor and evaluate their effectiveness regularly to identify gaps or areas of improvement which need to be addressed.
Evaluating and Updating Risk Management Strategies
- Risk Assessment: Conduct periodic risk assessments to detect emerging hazards associated with third-party relationships.
- Examine Existing Strategies: Identify gaps and opportunities for improvement in current risk management techniques.
- Develop and Implement New Strategies: Introduce enhanced risk-mitigation measures based on evolving threat landscapes.
- Regular Reviews and Updates: Establish a pre-set frequency for evaluating and updating risk management protocols.
Establishing Metrics and KPIs
- Number of Third-Party Relationships: Tracks engagements to measure program effectiveness.
- Risk Exposure: Evaluates the risk level associated with each third-party provider.
- Compliance Rate: Measures adherence to internal policies and regulatory obligations.
- Incident Response Time: Analyzes how quickly an organization reacts to security breaches involving third-party providers.
By continuously optimizing the third-party risk management lifecycle, organizations can strengthen their resilience, compliance, and security posture.
Conclusion
Establishing a suitable framework that you can adhere to is necessary if you want to create an efficient approach to the third-party risk management lifecycle. This guarantees that you establish the essentials, including as rules, processes, and systems, needed to deliver the risk management function with quality and consistency.
In conclusion, the lifespan of a third-party risk management life cycle begins before a contract is signed and lasts until the relationship is terminated and offboarded. To successfully identify and reduce your risks with third parties, you must have the proper processes and controls throughout the lifecycle.
Frequently Asked Questions
What is a Third Party Risk Lifecycle?
The third-party risk lifecycle is the process of identifying, assessing, mitigating, and monitoring the risks associated while working with third-party vendors or suppliers. A risk cycle involves evaluating the potential risks that third-parties pose to an organization’s operations, financial stability, and reputation. The life cycle typically includes steps like due diligence, contract negotiation, ongoing monitoring, and termination of the relationship if necessary.
What are the 5 phases of third party risk management?
The five phases of third-party risk management are:
- Planning and scoping: Defining the objectives, scope, and criteria for third-party risk management.
- Due diligence and third-party selection: Conducting due diligence to identify potential risks and selecting vendors or suppliers that meet the organization’s risk tolerance.
- Contract negotiation: Ensuring that contracts include appropriate terms and conditions to manage and mitigate third-party risks.
- Ongoing monitoring: Continuously monitoring third-party activities and performance to identify any new or emerging risks and to ensure ongoing compliance with contractual terms.
- Termination and offboarding: Managing the termination and offboarding of third-party relationships, including the return or destruction of data and assets, to minimize any residual risks.
Who is responsible for the third party lifecycle process?
The third party lifecycle process is typically looked after by an organization’s risk management function, which may include the risk management department, procurement department, or a dedicated third-party risk management team. In some cases, other departments such as legal, compliance, or information security may also be involved in the process.

