Third Party Risk Assessment – Checklist & Best Practices

Third Party risk management is a broad category that includes all of the steps your company can take to prevent data breaches and preserve business continuity. Some of the most typical third party risk assessment issues that all organizations examine on a regular basis are legal issues, historical performance, and creditworthiness. Furthermore, cybersecurity and reducing third-party security threats are becoming increasingly critical.
An effective third party risk assessment process guarantees that your vendor evaluation process is up to date, that sensitive information is protected, and that your organization’s risk management approach is improved.
Understanding Third-Party Risks
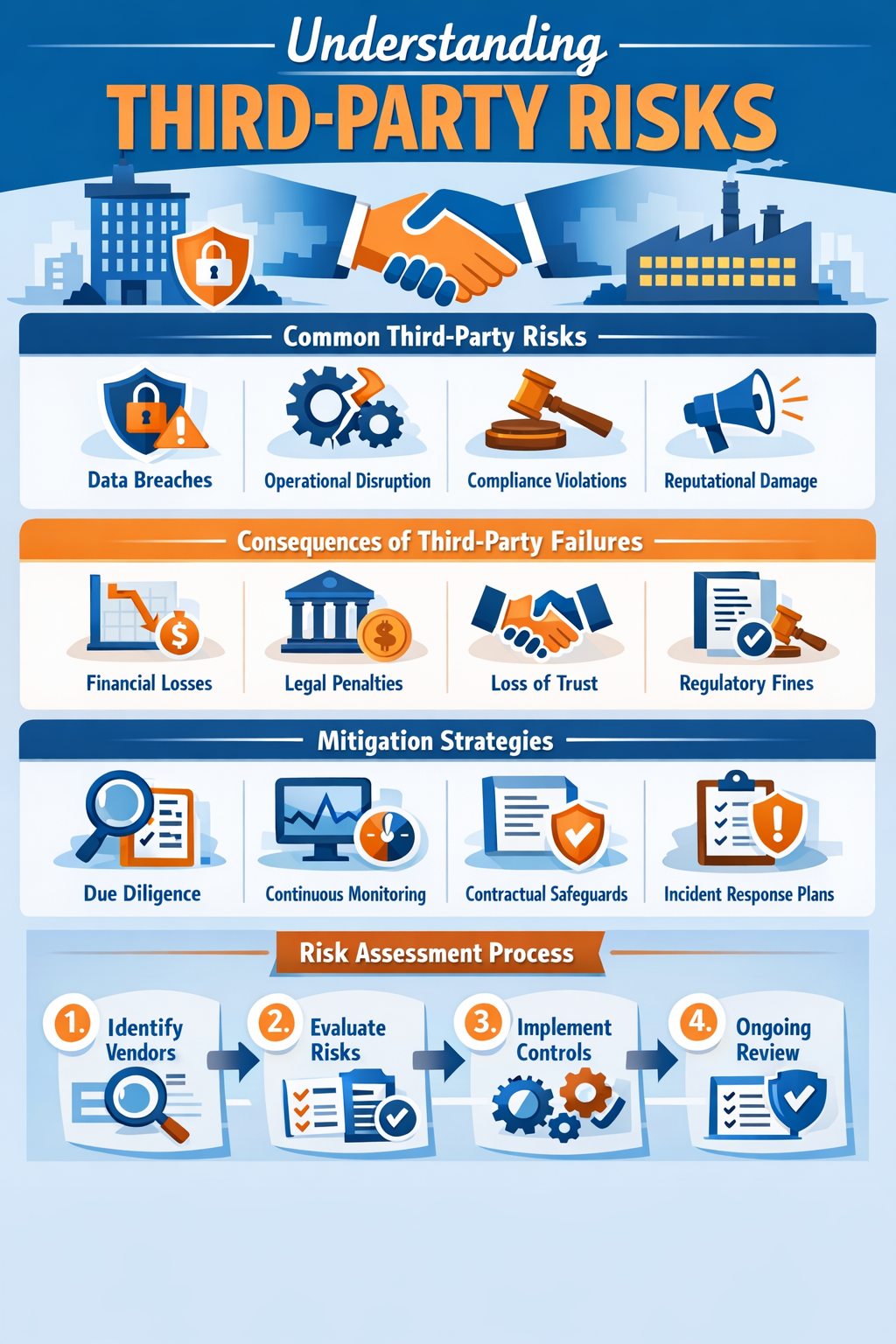
A third party is an external corporation or specialist that provides a service or specialization but is not a part of the organization. This includes a variety of services, including the following:
- Payrolling and human resources
- Computer data centers
- Cloud services
- Medical assistance
- Legal administration and many more.
Companies get more flexibility by outsourcing portions of corporate operations that require third-party partnerships rather than building an in-house workforce. Companies can avoid educating their specialists, lawyers, and doctors by collaborating with a third-party source.
However, due to businesses’ professional relationships with third-party vendors, these external agents will have access to important internal corporate data. A significant portion of the hazards is introduced here. This is why businesses must implement a dependable third party risk assessment program. This system will investigate and manage any risks that may occur due to the business relationship with a third-party vendor. These risks can have an impact on or compromise various parts of the business, including:
- Reputation
- Data privacy
- Legal
- Operations
Top 5 TPRM Predictions

As third-party risk management (TPRM) continues to evolve, 2025 will see an increasing emphasis on resilience, compliance, AI-driven insights, and cybersecurity. Here are the top five trends shaping the future of TPRM:
1. AI Will Revolutionize Risk Monitoring and Automation
The adoption of AI in TPRM will accelerate, enabling real-time risk analysis, predictive analytics, and automated documentation workflows. Organizations will increasingly rely on AI to detect inconsistencies, streamline due diligence, and enhance decision-making—provided robust governance is in place.
2. Tighter Regulations Will Demand Greater Transparency
Governments worldwide will expand data privacy, ESG, and resilience requirements, compelling organizations to assess vendor sustainability and operational risks more rigorously. Regulatory frameworks such as DORA, EU CSRD, and CSDDD will drive compliance harmonization and stricter third-party oversight.
3. Geopolitical Risks Will Increase Supply Chain Scrutiny
Ongoing global instability will push companies to analyze regional dependencies, identify concentration risks, and enhance vendor due diligence. Businesses will proactively monitor supplier networks to anticipate disruptions and ensure regulatory compliance.
4. TPRM Will Become an Enterprise-Wide Function
Risk management will expand beyond IT security teams, becoming embedded into procurement, sourcing, and enterprise risk management (ERM). Organizations will adopt a collaborative approach to address both cybersecurity and operational risks.
5. Third-Party Cyber Incidents Will Continue to Rise
With third-party breaches surging from 21% in 2021 to 60% in 2024, cybercriminals will expand their attacks to education, government, and manufacturing sectors. Strengthening vendor security practices and continuous monitoring will be critical.
Lines of Defense for third party risk assessment
Establishing three lines of defense is a great method for managing the risks of third-party collaborations. This will serve as a roadmap for quick and decisive responses to threats.
1. Front Line of Defense – Business Units
The first line of defense consists of individual business units responsible for managing third-party partnerships. Third-party providers play a self-regulatory role, identifying, mitigating, and analyzing vendor risks while aligning with the company’s risk management policies.
2. Second Line of Defense – Risk Assessment & Compliance
The second line of defense is the third-party risk assessment program, which oversees risk frameworks and policies. This team conducts vendor due diligence, enforces risk mitigation strategies, and ensures third-party providers comply with corporate regulations and industry standards.
3. Third Line of Defense – Independent Audit
The third line of defense involves independent third-party risk audits, evaluating the effectiveness and cost-efficiency of internal policies. Auditors assess risk management frameworks, generate compliance reports, and recommend improvements to strengthen third-party governance.
By implementing the three lines of defense model, organizations can enhance third-party risk management (TPRM), improve compliance, and safeguard against operational and financial vulnerabilities.
How Do You Perform a Third party Risk Assessment?
The assessment of third-party risk is an essential part of a comprehensive vendor management program. This assessment can take place during the vetting phase, or during an evaluation or review to continuously measure performance.
Throughout the vendor lifecycle, organizations should also provide vendor report reviews that support and document ongoing governance.
What should be included in a third party risk assessment checklist?
A third party risk assessment checklist should incorporate a variety of security protocols that will safeguard your network and your business. A third-party risk assessment begins with the following:
The Business Model
The processes, policies, procedures, and people in place to govern your vendor management processes are referred to as the operational model. Most businesses today divide their processes into three lines of defense (LOD):
- Business line – creates, owns, and manages risk.
- Support functions – supervises the front line. Also encompasses operational risk, compliance, and other risk disciplines.
- Internal audit – the board’s mandate to process-audit the first and second lines of defense.
Any third party risk assessment program is based on the lines of defense, along with vendor risk assessment documents that outline their functions.
To assess your operating model and documentation, let’s take a closer look at the checks you can perform.
Third Party Risk Assessment Policy
- Has an organized and simple method of evaluating information value
- Has a documented and established vendor risk assessment methodology
- Identifies and prioritizes assets
- Identifies common dangers
- Vulnerabilities are identified.
- Includes a fair and consistent method of evaluating vendors.
- Analyzes, regulate, and determine whether updates or additional controls are required.
- Calculates the effect of possible scenarios
- Risk is prioritized based on its importance and cost.
- All risk assessment outcomes are documented.
- Utilizes a tried-and-true security questionnaire
Other critical components include:
- Third party risk assessment policy, in which vendors are classified based on their risk.
- third party risk assessment procedures – outlines the steps required to conduct a vendor management review.
- Continuous governance entails examining audit reports and policies.
What should be in a third party risk assessment policy?
It is critical to ensure a robust IT ecosystem while designing your organization’s third party risk assessment policy. Senior management should thoroughly evaluate each new vendor, from ensuring that the finest cybersecurity procedures are used to ensuring that compliance needs are satisfied.
Minimum criteria should be established for certain areas such as human resources, network and data security, access control, IT acquisition, and maintenance. Vendors should also be obliged to have their own risk management program outlining their obligations for incident response, business continuity, and catastrophe recovery.
Each third party risk assessment policy should specify the vendor compliance and review requirements, which may include SOC 2 audits and/or site visits.
Your team should go through a rigorous procedure when selecting the correct vendors: Each new vendor should be able to demonstrate its own procedural risk management strategies, in addition to demonstrating outstanding information security processes.
Your vendor connections may have the ability to quickly accelerate your business objectives, but they must first be evaluated in order to avoid excessive risk for your corporation.
Best Practices to Prepare for and Conduct a Third Party Risk Assessment
Follow the best practices below to conduct a thorough risk assessment:
- Prior to the vetting step, you should have a clear grasp of your business objectives and risk tolerance.
- Check for vendor dependability during the vetting process utilizing a range of ways, such as background checks, customer reviews, and referrals from reputable sources.
- Make a list of all current vendors and categorize the list (e.g., healthcare, payment processors, office services, etc.).
- Check your vendor list against the list kept by your accounting department to check that all vendors are listed.
- Determine which vendors have the most influence on your business (for example, do you consider a third party to be vital or non-critical?).
- Assign a risk rating to each vendor (from moderate to critical) based on the vendor’s potential to cause regulatory compliance issues, data security problems, or financial risk to your firm.
- Determine the continuing due diligence you must undertake on each vendor based on their level of risk and concentrate your efforts on high-impact vendors who offer a medium-to-high risk to your firm.
- Gather information from internal subject matter experts and stay up to date on changing legislation and guidelines so that questionnaires and risk assessments may be updated accordingly.
- Standardize your third party management programme to maintain streamlined and efficient procedures.
- Conduct regular due diligence assessments and assess the efficiency of your vendor management approach.
How SignalX Enhances Third-Party Risk Assessment
SignalX plays a pivotal role in enhancing third-party risk assessment through its AI-powered risk intelligence platform. By automating over 200 risk checks, SignalX provides organizations with comprehensive insights into potential vendor-related risks, ensuring informed decision-making and robust risk management.
1.Automated Due Diligence: SignalX streamlines the vendor evaluation process by automating due diligence checks, covering financial stability, legal compliance, cybersecurity posture, and reputational factors. This automation reduces manual effort and accelerates the onboarding of new vendors.
2.Continuous Monitoring: Beyond initial assessments, SignalX offers continuous monitoring of third-party vendors. It tracks changes in vendor risk profiles in real-time, alerting organizations to emerging threats or compliance issues, thereby enabling proactive risk mitigation.
3.Risk Scoring and Tiering: The platform assigns risk scores to vendors based on various parameters, allowing organizations to categorize vendors into risk tiers. This classification aids in prioritizing risk management efforts and allocating resources effectively.
4.Comprehensive Risk Assessment Checklists: SignalX provides detailed checklists and policy templates for third-party risk assessments, ensuring that organizations consider all critical aspects, including data protection, regulatory compliance, operational resilience, and contractual obligations.
5.Integration with Existing Workflows: Designed to seamlessly integrate with an organization’s existing vendor management processes, SignalX enhances efficiency without disrupting established workflows.
By leveraging SignalX, organizations can transition from reactive to proactive third-party risk management, ensuring that vendor-related risks are identified, assessed, and mitigated effectively throughout the vendor lifecycle.
For a more detailed exploration of SignalX’s offerings and to access their third-party risk assessment resources, you can visit their
Book A Demo With SignalX For Third Party Risk Assessment
Tips For Developing a third party risk assessment Questionnaire
As you develop and revise your third party risk assessment questionnaires as part of your overall vendor management program, the following tips will provide you with guidance.
- Customize Each Questionnaire for Each Vendor: Your third party risk assessment strategy should not be one-size-fits-all. Questions should focus on the types and level of risk a vendor poses to your business, the products and services a vendor provides, and the influence a vendor has on your day-to-day business operations. A typical set of questions may suffice for low-risk, low-impact providers. Expand on the normal set of questions for high-risk, high-impact vendors to add concerns about access to confidential information. Simply put, only ask inquiries about the type of provider with whom you’re working.
- Use straightforward language: Make the directions clear and the questions short. Keep technical jargon to a minimum. Any misunderstanding of a query may result in inaccurate or inefficient results.
- Consult Regulatory Guidance and Subject Matter Experts: The questions will differ depending on the vendor’s industry and the guidelines imposed by the applicable governing regulatory organizations. The principles and regulations will assist you in categorizing and developing your list of questions. In addition to researching current rules, consult with relevant internal subject matter experts for guidance on which questions to include.
- Structure Your Questionnaire Using Important Categories for Your Organization: Using the knowledge gained in the previous stage, structure your questionnaire into categories that are important to your company and relevant to the vendor. You’ll stay organized and make the best use of your time and resources this way.
- On a regular basis, update the Questionnaire: Determine how frequently you will review and alter your questionnaire in light of changing legislation and vendor risks. A monthly evaluation ensures that the questions you ask are still relevant to the threats your company confronts.

