Third-Party Vendor Security Assessment Checklist: What You Need to Know

In the modern digital economy, organizations no longer work alone. They collaborate, integrate, outsource, and depend on a web of third-party vendors from cloud hosting providers and SaaS platforms to payroll processors, consultants, and analytics tools. These relationships unlock efficiency, innovation, and scalability.
But they also introduce a new challenge, security vulnerabilities that originate outside your organization but impact you directly.
A vendor with poor cybersecurity practices can become the weakest link in your entire ecosystem. One overlooked vendor risk can expose sensitive data, disrupt operations, trigger non-compliance penalties, and damage your brand reputation.
This is why Third-Party Vendor Security Assessments are now a business necessity, not a luxury.
This comprehensive, humanized guide walks you through why these Third-Party Vendor Security Assessments are essential, provides a detailed checklist, and shows how SignalX can transform your vendor risk management process with automation and continuous monitoring.
Why a Third-Party Vendor Security Assessment Is Compulsory
Because cybercriminals now target vendors not just big companies:
Instead of attacking your hardened defenses, attackers often breach smaller vendors who have access to your systems or data. This “island-hopping” strategy has been behind major global cyberattacks.
Because regulatory bodies demand it: GDPR, HIPAA, SOC 2, ISO 27001, and PCI-DSS all require organizations to validate vendor security controls.
Because your data travels further than you think: From CRM tools to marketing platforms, every tool your team uses potentially handles sensitive information.
Because downtime caused by a vendor outage for your customers: A vendor outage can cripple your internal operations and service delivery.
Because customer trust depends on strong vendor oversight, Customers don’t differentiate between you and your vendors. A vendor breach is perceived as your breach.
Book Demo: Third-Party Vendor Security Assessment
The Complete Third-Party Vendor Security Assessment Checklist
Use this checklist to evaluate vendors before onboarding and throughout the relationship.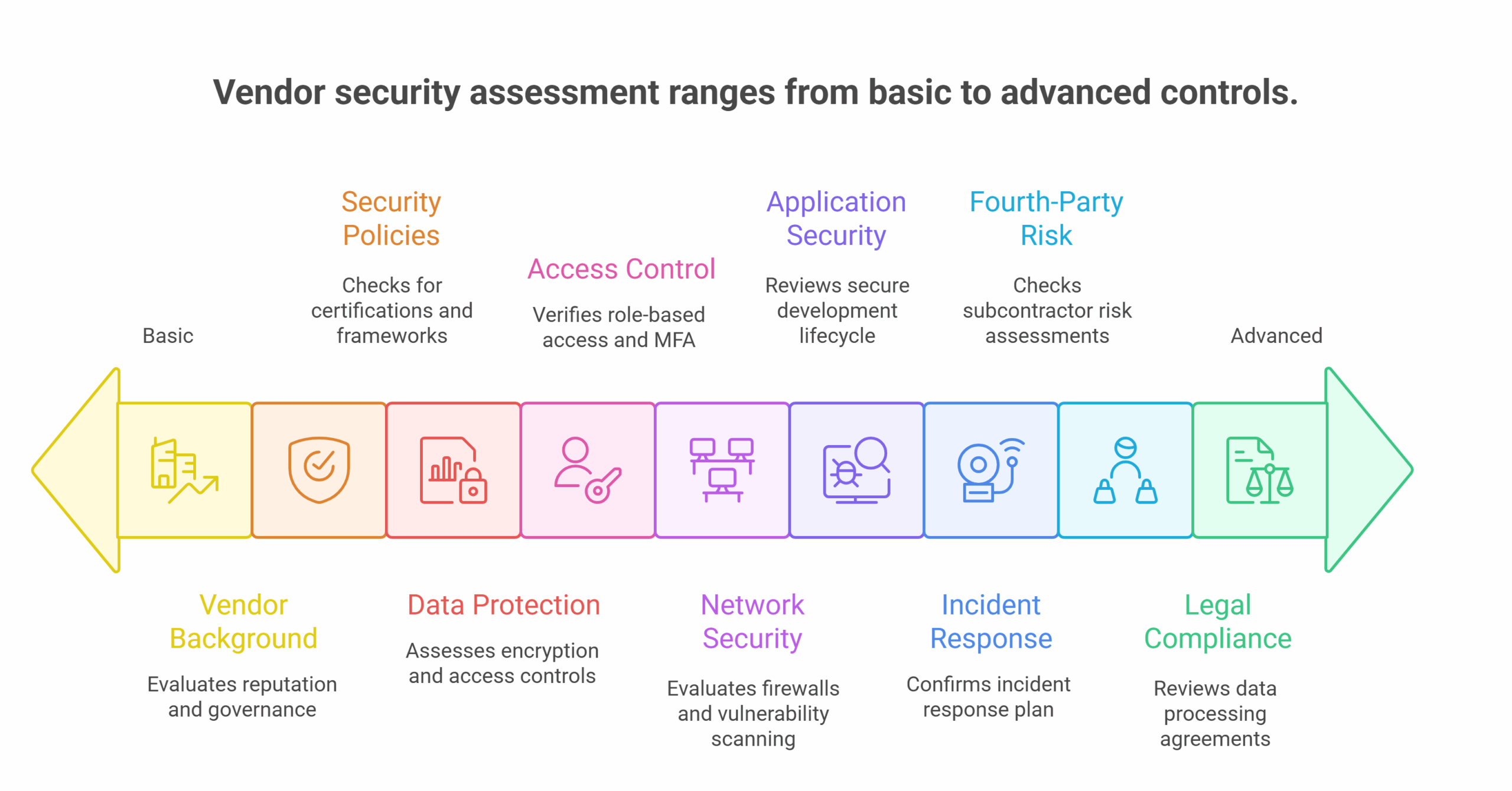 1. Vendor Background & Governance
1. Vendor Background & Governance
A secure vendor must have strong foundations.
Evaluate:
- Company reputation, history, and stability
- Ownership and governance structure
- Past security incidents or legal disputes
- Leadership experience in security
- Documentation of internal controls
A vendor with unstable operations or repeated incidents increases your risk exposure.
2. Information Security Policies & Frameworks
A competent vendor follows globally recognized security frameworks.
Check for:
- ISO 27001 certification
- SOC 2 (Type I or II) reports
- NIST Cybersecurity Framework compliance
- Well-defined information security policies
- Employee cybersecurity training
- These controls reflect the seriousness of their cybersecurity commitment.
3. Data Protection & Privacy Controls
If your vendor handles sensitive or personal data, this section is crucial.
Assess:
- Encryption standards (data at rest & in transit)
- Access restrictions to sensitive data
- Data minimization techniques
- GDPR/CCPA compliance
- Well-defined retention & deletion policies
- Proper data protection drastically reduces breach probability.
4. Access Control & User Management
Unauthorized access remains one of the top causes of data breaches.
Check for:
- Role-based access control (RBAC)
- Multi-factor authentication (MFA)
- Strict password policies
- System access logging
- Regular access reviews
- Strong access control limits internal misuse and external compromise.
5. Network & Infrastructure Security
A secure network is the backbone of strong cybersecurity.
Evaluate:
- Firewalls and IDS/IPS
- Network segmentation
- Regular vulnerability scanning
- Patch/update management
- Secure cloud configurations
- Outdated networks create exploitable gaps.
6. Application Security (for SaaS Vendors)
Most vulnerabilities arise at the application level.
Review:
- Secure development lifecycle (SDLC)
- OWASP Top 10 coverage
- API testing and protections
- Code review process
- Penetration test reports
This ensures your vendor’s product won’t expose your data.
7. Incident Response & Breach Handling
A breach may not be preventable but the damage is controllable.
Confirm:
- Documented incident response plan
- Clear notification timelines
- Dedicated IR team
- Forensic investigation procedures
- Continuous security monitoring capabilities
- Response readiness shortens breach impact dramatically.
- 8. Fourth-Party & Sub-vendor Risk
Your vendor’s vendor can expose you often without your knowledge.
Check whether:
- Subcontractors are disclosed
- The vendor performs risk assessments on them
- They notify you before onboarding new sub-vendors
- Fourth-party risk is one of the most overlooked threat vectors.
9. Legal, Contractual & Compliance Requirements.
Your contract must hold vendors accountable.
Review:
- Data processing agreements (DPA)
- Security and confidentiality clauses
- Compliance obligations
- Liability and indemnity clauses
- Right-to-audit permissions
- Strong contracts protect you even when something goes wrong.
Advantages of Third-Party Vendor Security Assessment
Performing vendor security assessments delivers far-reaching benefits that directly shape your organization’s security posture, operational resilience, and regulatory alignment.
1. Identifies Hidden Vulnerabilities Before They Hurt You
Assessments uncover security gaps weak access controls, outdated systems, unsecured APIs before attackers exploit them. This early detection prevents invisible threats from entering your environment.
2. Builds a Strong, Secure Vendor Ecosystem
When vendors know you actively monitor their security, they step up their cybersecurity efforts. This creates a healthier, stronger third-party ecosystem around your business.
3. Protects Your Brand Reputation
A breach via a vendor damages trust even if it wasn’t your fault. Security assessments reduce the chances of such incidents and preserve customer confidence.
4. Reduces Financial Losses and Legal Exposure
Data breaches bring: Regulatory fines, Operational disruption, lawsuits, and customer compensation. Assessments drastically reduce these risks.
5. Keeps You Audit-Ready at All Times
With documented vendor assessments, you can prove compliance instantly during external audits. This builds credibility with regulators and partners.
6. Enables Better Vendor Selection & Renewal Decisions
Security becomes a measurable factor not a guess.
You can choose vendors with strong cybersecurity fundamentals and discontinue relationships with risky ones.
7. Strengthens Organizational Resilience
When vendors have strong controls, your operations become more stable, reliable, and resistant to cyber threats.
How SignalX Powers Smarter Third-Party Vendor Risk Management
SignalX elevates how organizations manage vendor security by combining automation, intelligence, and continuous monitoring into one seamless platform.
Their capabilities specifically enhance the Third-Party Vendor Risk Management Policy Template by offering practical workflows for assessment and ongoing monitoring.
1. Professionally Designed Policy Templates
SignalX simplifies onboarding and compliance with:
- Vendor risk assessment templates
- Continuous monitoring frameworks
- Pre-built onboarding policies
- ISO/NIST/SOC2-aligned documentation
This accelerates implementation and ensures best-practice consistency.
2. Automated Assessment Workflows
SignalX dramatically reduces manual work by:
- Automatically generating vendor questionnaires
- Scoring responses using intelligent logic
- Highlighting high-risk areas instantly
- Suggesting remediation steps
You save time and gain clarity without spreadsheet chaos.
3. Continuous Monitoring & Real-Time Alerts
Instead of waiting for annual reviews, SignalX monitors:
Cybersecurity posture
- Legal & compliance changes
- Financial stability
- Breach reports
- Negative media updates
You stay informed the moment something changes.
4. Unified Vendor Intelligence Dashboard
SignalX consolidates:
- Cyber risk scores
- Legal red flags
- Operational performance signals
- Financial health indicators
- Sub-vendor risk visibility
This 360° view helps you make confident, data-driven decisions.
5. Actionable Remediation Guidance
SignalX doesn’t just identify risks it shows you how to fix them.
- Control recommendations
- Prioritized action plans
- Remediation progress tracking
- Policy improvement tips
This closes the loop between assessment and action.
Conclusion
Third-party vendors are critical assets but they can also be potential security liabilities if unmanaged.
A strong Third-Party Vendor Security Assessment Checklist helps you evaluate, monitor, and manage vendor risks systematically and confidently.
With SignalX, you move from manual, inconsistent, spreadsheet-driven vendor risk management to an automated, intelligent, always-on system that keeps your organization secure and compliant.
Ready to elevate your Third-Party Vendor Security Assessment?
Grab your Questionnaire copy and strengthen your risk evaluation today.
Discover how SignalX can help you automate assessments, continuously monitor vendor risks, and protect your business from supply-chain threats.
