What Are Third-Party Vendor Risks? Types, Examples, and How to Manage Them

Modern businesses rarely operate alone. From cloud hosting providers and payment processors to marketing agencies and payroll vendors, organizations rely on dozens sometimes hundreds of third parties to function. While outsourcing increases speed and efficiency, it also introduces a growing and often underestimated threat: third-party vendor risk.
High-profile data breaches, regulatory fines, and operational outages increasingly trace back not to internal failures, but to vendors and subcontractors. As a result, third-party risk management (TPRM) has shifted from a checkbox compliance exercise to a strategic business priority.
This guide explains what third-party vendor risks are, why they matter, the different types of risks organizations face, and how modern companies use technology like SignalX to manage vendor risk continuously and at scale.
What Is Third-Party Vendor Risk?
Third-party vendor risk refers to the potential harm an organization may face due to its relationships with external vendors, suppliers, contractors, or service providers.
In simple terms, when you give a vendor access to your systems, data, customers, or critical operations, you inherit part of their risk profile. If that vendor experiences a cyber breach, financial collapse, compliance failure, or service outage, your organization may suffer the consequences even if you did everything right internally.
Third-Party vs. Supplier vs. Fourth-Party Risk
While these terms are often used interchangeably, there are important distinctions:
Third-party risk: Risk arising from vendors you contract with directly
Supplier risk: Often refers specifically to vendors in supply chain or manufacturing contexts
Fourth-party risk: Risk introduced by your vendors’ subcontractors and service providers
For example, if your payroll provider uses a cloud infrastructure company that suffers an outage, that is a fourth-party risk yet your business still feels the impact.
Why Third-Party Vendor Risks Matter for Businesses
Third-party failures rarely stay contained. When a vendor experiences an issue, the ripple effects can be immediate and costly.
Financial Impact
Vendor incidents can lead to direct losses through fraud, business interruption, contract penalties, or lost revenue. In regulated industries, fines and remediation costs can escalate quickly.
Regulatory and Compliance Exposure
Many regulations including GDPR, HIPAA, SOC 2, and ISO 27001 hold organizations accountable for how vendors handle sensitive data. “The vendor caused it” is not a valid defense.
Operational Disruption
If a critical vendor goes offline, your business operations may stall. This is especially risky when vendors support customer-facing systems or core infrastructure.
Reputational Damage
Customers rarely distinguish between you and your vendors. A breach, outage, or ethical failure at a third party can erode trust in your brand overnight.
Example:
A SaaS company outsources customer support to a third party. That vendor mishandles customer data, triggering a breach notification. Even though the SaaS company wasn’t directly responsible, customers associate the failure with the brand.
Types of Third-Party Vendor Risks
Cybersecurity and Data Privacy Risk
Vendors can introduce security weaknesses through poor cyber hygiene, outdated systems, weak access controls, or inadequate incident response capabilities. Any third party with access to sensitive data or internal systems can become an entry point for cyberattacks and data breaches.
Financial and Solvency Risk
A vendor experiencing financial instability may struggle to maintain service quality, delay critical investments, or abruptly cease operations. This can result in service disruption, increased operational risk, and unexpected replacement costs for your organization.
Regulatory and Compliance Risk
When vendors fail to comply with industry standards or regulatory requirements, your organization may face audits, fines, legal penalties, or enforcement actions. Non-compliance by a vendor can directly transfer regulatory exposure to your business.
Operational and Business Continuity Risk
Operational disruptions at a vendor caused by natural disasters, workforce issues, system outages, or ineffective internal processes—can interrupt your critical business functions. These failures may impact service availability, customer experience, and overall resilience.
Legal and Contractual Risk
Unclear contractual terms, missing service-level agreements, or insufficient liability provisions can weaken your ability to enforce expectations. This increases the risk of disputes and limits your ability to recover losses when vendor failures occur.
Reputational and ESG Risk
Vendor actions related to ethics, labor practices, environmental responsibility, or public controversies can negatively affect your brand. Reputational damage often occurs quickly and can persist even if your organization was not directly responsible.
Fourth-Party and Subcontractor Risk
Vendors often rely on subcontractors to deliver services, creating additional layers of dependency and risk. Limited visibility into these fourth-party relationships can hide vulnerabilities that may impact your operations.
Geopolitical and Country Risk
Vendors operating in politically unstable regions or under changing regulatory regimes may face sanctions, trade restrictions, or government intervention. These factors can disrupt service delivery and introduce unexpected compliance and operational challenges.
The Third-Party Risk Management Lifecycle
Effective third-party risk management is not a one-time task it’s a continuous lifecycle.
1. Vendor Identification and Classification
Organizations first identify all vendors and classify them based on risk factors such as data access, business criticality, and regulatory impact.
2. Risk Assessment and Due Diligence
Before onboarding, vendors are assessed through questionnaires, document reviews, and external intelligence to evaluate their risk posture.
3. Risk Scoring and Prioritization
Not all vendors deserve equal scrutiny. Risk scoring helps teams focus attention where it matters most.
4. Ongoing Monitoring and Alerts
Vendor risk evolves. Continuous monitoring detects changes such as financial distress, security incidents, or regulatory violations.
5. Remediation and Risk Mitigation
When issues arise, organizations work with vendors to remediate gaps or apply compensating controls.
6. Offboarding and Termination
When relationships end, access must be revoked, data returned or destroyed, and risks formally closed.
How Organizations Traditionally Manage Vendor Risk
Historically, vendor risk management has relied on:
- Manual security questionnaires
- Spreadsheet-based tracking
- Annual or biennial reviews
- Static risk reports
While these methods may satisfy baseline compliance requirements, they suffer from major limitations.
Limitations of Traditional Approaches
- Point-in-time assessments miss emerging risks
- Manual processes don’t scale as vendor counts grow
- Self-reported data may be incomplete or outdated
- Delayed visibility leaves teams reacting instead of preventing
In today’s fast-changing risk environment, annual reviews are no longer sufficient.
How Technology Platforms Help Manage Third-Party Vendor Risk
Technology platforms play a critical role in strengthening third-party risk management by replacing manual, time-consuming processes with automation, intelligence, and continuous oversight. Through automation, organizations can streamline repetitive activities such as sending questionnaires, collecting evidence, and tracking vendor responses, significantly reducing operational effort and delays. Continuous monitoring capabilities ensure that vendor risk is assessed on an ongoing basis rather than at fixed intervals. AI-driven analytics further enhance this process by evaluating trends across financial performance, cybersecurity incidents, regulatory developments, and publicly available information to identify potential risks before they escalate.
In addition, modern platforms integrate external data sources such as breach notifications, sanctions databases, credit signals, and cyber intelligence providing a more objective and comprehensive risk view that does not rely solely on vendor self-disclosures. Together, these capabilities enable faster vendor onboarding and more efficient risk assessments while preserving rigorous governance and control.
Where SignalX Fits in Third-Party Risk Management
SignalX approaches third-party risk from a risk intelligence-first perspective.
Rather than focusing solely on compliance checklists, SignalX delivers automated due diligence and continuous vendor risk insights powered by AI and external data signals.
What Makes SignalX Different
- Automated vendor profiling without endless questionnaires
- Continuous monitoring across cyber, financial, regulatory, and operational risk
- Real-time alerts when vendor risk changes
- Faster assessments with minimal vendor friction
Ideal Customers
SignalX is designed for:
- Compliance and risk teams seeking proactive risk visibility
- Procurement teams managing large vendor ecosystems
- Security leaders needing early warning signals
Growing companies that want enterprise-grade insight without enterprise complexity
SignalX Competitor Landscape
The vendor risk management market includes a range of tools with different strengths:
- Vanta – Compliance-first platform focused on SOC 2 and security readiness
- AuditBoard – Enterprise-grade GRC with audit and risk workflows
- Secureframe – SOC 2–driven compliance and vendor assessments
- UpGuard – External security posture and attack surface monitoring
- LogicManager – Broad ERM platform with vendor risk modules
Each serves a different maturity level and risk philosophy.
SignalX vs Competitors (High-Level Comparison)
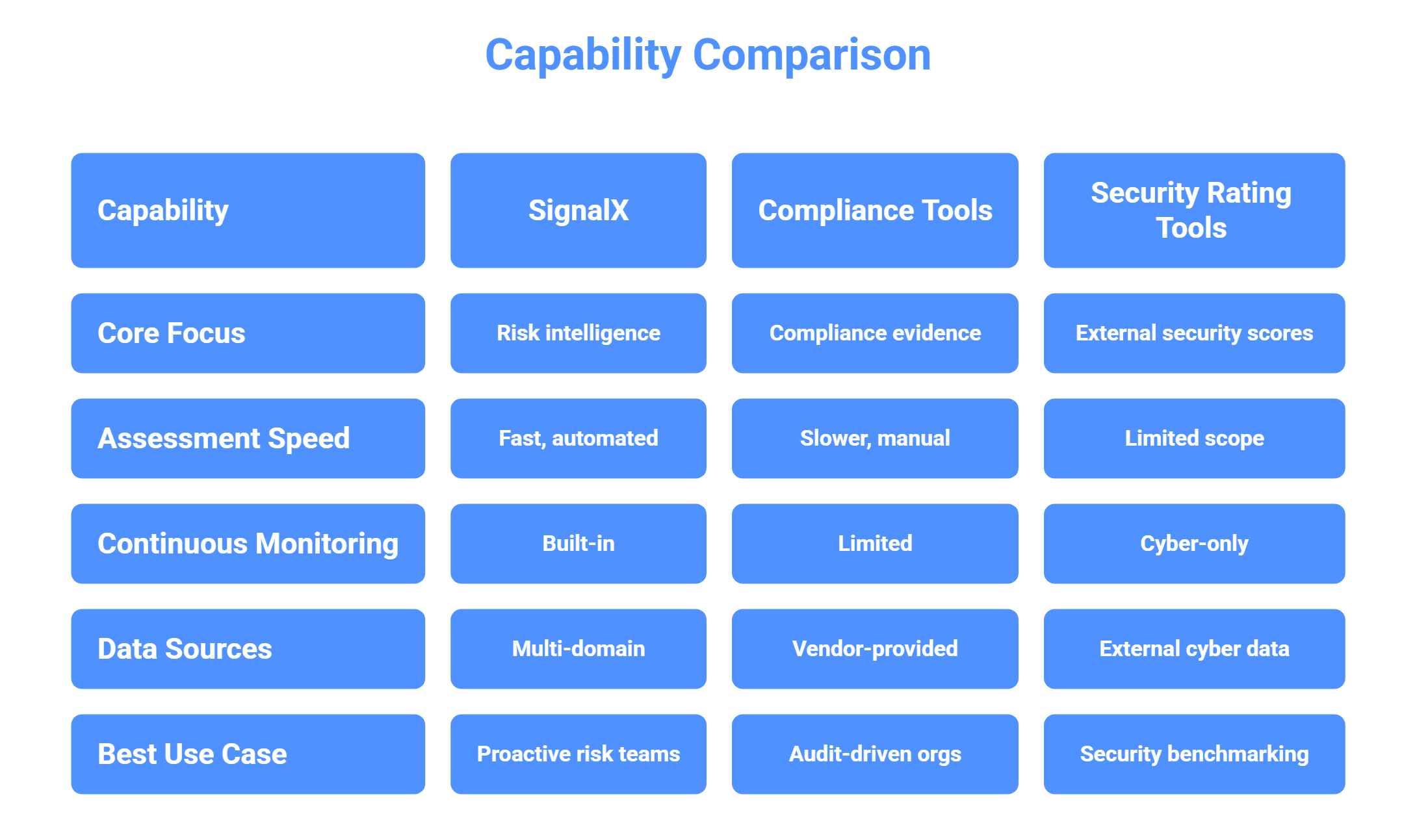
SignalX is ideal when organizations need real-time risk visibility, not just compliance documentation.
How to Choose the Right Third-Party Risk Management Tool
Selecting the right tool depends on your organization’s size, risk exposure, and maturity.
Key Evaluation Criteria
Depth of risk coverage (cyber, financial, regulatory)
Continuous vs. periodic monitoring
Automation and AI capabilities
Ease of vendor onboarding
Reporting and alerting flexibility
Questions to Ask Vendors
How do you detect emerging vendor risks?
What external data sources do you use?
How often are risk signals updated?
Can the platform scale as our vendor count grows?
Lightweight vs. Enterprise GRC
Smaller or fast-growing organizations often benefit more from AI-driven risk intelligence platforms than heavy enterprise GRC tools designed for audit-heavy environments.
Third-Party Vendor Risk Assessment Checklist
Pre-Engagement Checks
- Vendor ownership and business model
- Financial stability indicators
- Geographic and regulatory exposure
Security and Data Protection
- Data handling practices
- Access controls and encryption
- Incident response capabilities
Financial and Legal
- Contract terms and SLAs
- Liability and indemnification clauses
- Insurance coverage
Ongoing Monitoring
- Security incidents and breaches
- Regulatory actions
- Financial distress signals
Red Flags Requiring Escalation
- Sudden changes in ownership
- Repeated security incidents
- Failure to remediate known issues
Best Practices for Reducing Third-Party Vendor Risk
Reducing third-party vendor risk starts with recognizing that not all vendors pose the same level of exposure. Organizations should classify vendors based on both their criticality to business operations and the level of risk they introduce, allowing resources and oversight to be applied where they matter most. Risk management should then be built directly into vendor contracts by clearly defining security requirements, compliance expectations, audit rights, and consequences for non-performance.
Rather than relying on periodic or annual reviews, organizations benefit from ongoing monitoring that can detect changes in a vendor’s risk posture in near real time. Clear accountability is also essentialspecific internal owners should be designated to manage vendor relationships and respond quickly if incidents occur. Finally, true risk visibility extends beyond direct vendors; organizations must understand and track fourth-party dependencies to ensure that risks introduced through subcontractors and service chains are identified and managed proactively.
Frequently Asked Questions
What is a third-party vendor risk?
It is the risk your organization faces due to failures, breaches, or issues at external vendors you rely on.
How often should vendors be reassessed?
High-risk vendors should be monitored continuously, with formal reassessments at least annually.
What is continuous vendor monitoring?
Ongoing tracking of vendor risk signals such as cyber incidents, financial distress, or regulatory changes in real time.
Are small businesses exposed to third-party risk?
Yes. Smaller companies often rely more heavily on vendors and may have less margin for error.
What is the difference between third-party and fourth-party risk?
Third-party risk comes from your direct vendors; fourth-party risk comes from your vendors’ vendors.
Conclusion
Third-party vendor risk is no longer a back-office concern it’s a core business risk that affects security, compliance, operations, and reputation. As vendor ecosystems grow more complex, organizations need more than static assessments and spreadsheets.
Modern third-party risk management requires continuous, automated, and intelligence-driven approaches that surface risks before they turn into incidents.
If your organization is ready to move beyond manual reviews and reactive workflows, explore how SignalX delivers real-time vendor risk intelligence, faster assessments, and proactive insights so you can manage third-party risk with confidence.


