In today’s interconnected business landscape, third-party risks have become increasingly prevalent. Due to third-party security breaches that recently dominated the headlines, many organizations are re-emphasizing the importance of effective third party risk management (TPRM). This article will provide an overview of key concepts and best practices to help organizations get started with Third Party Risk Management.
Who is a Third-Party?
A third party is any company or person with whom you have a business relationship: offering goods and services, carrying out outsourced tasks, or accessing markets and products. In short, a third-party vendor is a person or corporation who sells services to another firm (or the clients of that company).
What is Third-Party Risk?
Third party risk refers to the probability of your company to experience a negative event (such as a data breach, a disruption in operations, or reputational damage) when you outsource specific services or use software produced by third parties to do specific tasks and activities.
These risks can arise due to several factors and have the potential to make a huge impact on the company.
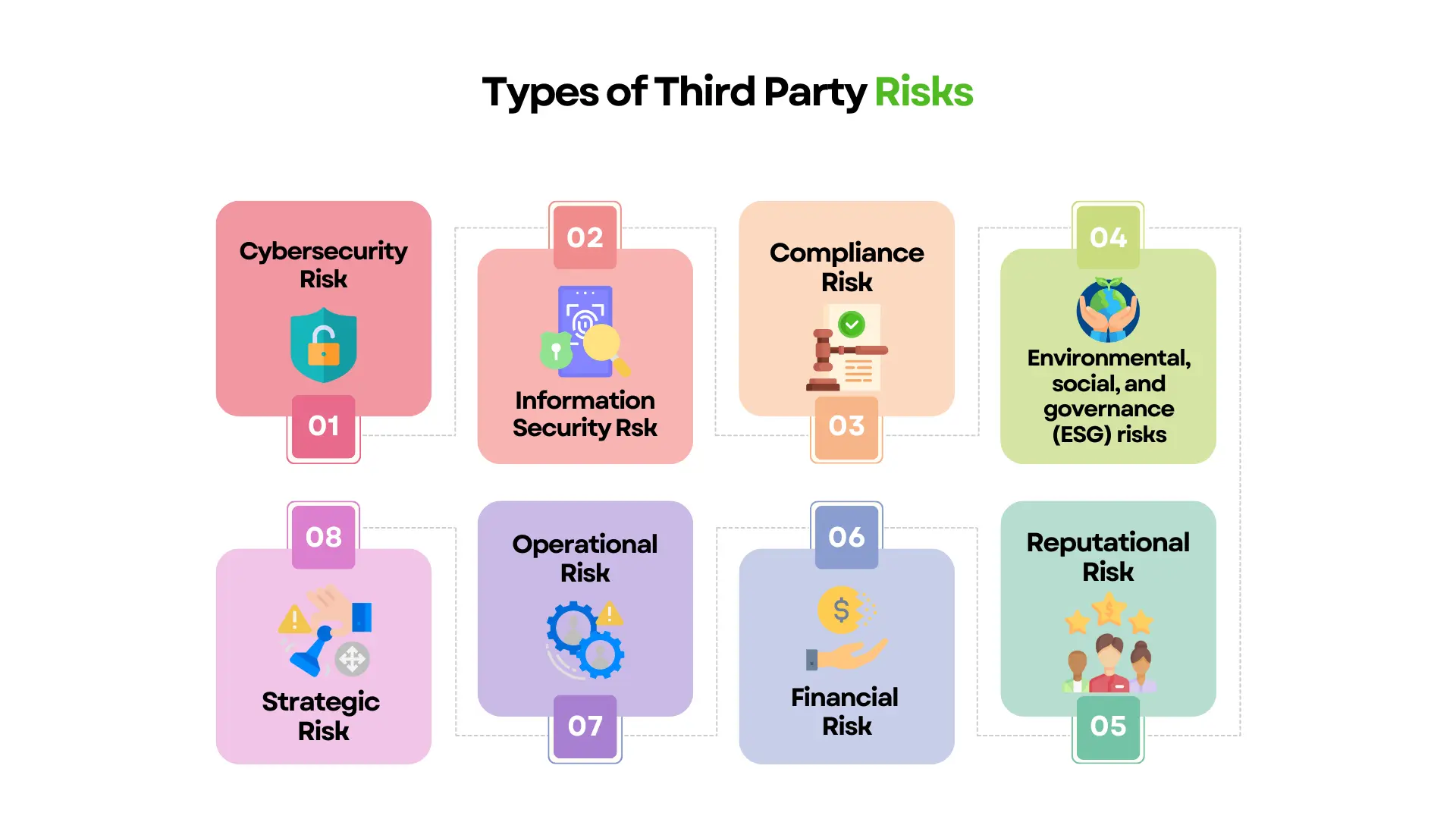
Types of Third-Party Risks
1. Cybersecurity risk
With the sophistication and speed of cyber threats increasing, it is more vital than ever to assess your vendor’s cybersecurity posture. You must first assess your organization’s risk tolerance before evaluating vendor cybersecurity risk.
After determining acceptable risk levels, you can begin reviewing third-party security performance and making necessary modifications. When assessing performance, concentrate on compromised systems within vendor network settings. While hacked systems do not result in data loss, they do reveal how vendors detect and mitigate intrusions.
2. Information security risk
Information security risk relates to ransomware, malware, data breaches, and cyber incidents caused by unauthorized third-party access to systems and devices. These dangers can also result from inadequate or ineffective cybersecurity protections. Limiting vendor access and controls to sensitive business information and customer personally identifiable information is critical to ensuring your company secures sensitive information at all costs.
3. Compliance risk
Infractions of laws, regulations, and internal processes that your organization must follow in order to conduct business constitute compliance risk. The laws that apply to each organization will vary depending on their industry; however, there are some basic regulations that apply to all businesses. Non-compliance with these standards frequently results in significant fines, thus it is critical that you ensure that your vendor’s compliance activities line with regulatory requirements.
4. Environmental, social, and governance (ESG) risks
ESG risks exist when vendors violate your organization’s specific rules or policies regarding environmental effect, resource use, employee treatment, or other sustainability measures. If your third-party vendors fail to follow ESG rules, your organization may face the consequences of human rights breaches, compliance concerns from inadequate supply chain management, or other threats to business continuity.
5. Reputational risk
The public perception of your firm is the focus of reputational risk. Third party sellers can hurt your reputation in a variety of ways, including:
- Interactions that do not adhere to business requirements
- Customer information loss or disclosure as a result of carelessness or a data breach
- Law and regulation violations
6. Financial risk
Third-party financial risk is created when suppliers don’t meet your company’s expectations for financial performance. Vendors face two types of financial risk: exorbitant expenditures and missed revenue.
Excessive costs, if not addressed, can stymie firm growth and lead to excessive debt. To keep expenses under control, you should conduct a financial due diligence at the time of the vendor screening and onbaording and also perform frequent audits to ensure that vendor expenditure is in accordance with the terms of your contract.
7. Operational risk
When vendor procedures are shut down, operational risk occurs. Third-party operations are inextricably linked to organizational operations, thus when vendors fail to deliver on their promises, organizations frequently fail to carry out their everyday operations.
To reduce operational risk, your organization should develop a business continuity strategy so that you can continue to operate in the case of a vendor shutdown.
8. Strategic risk
Strategic risks develop when vendors make commercial decisions that do not correspond with your organization’s strategic objectives. Strategic risk can impact compliance and reputational risk, and it is frequently a determining element in a company’s total worth. Establishing KPIs allows organizations to efficiently monitor strategic risk by providing useful information into vendor operations and processes.
What is Third Party Risk Management?
Third party risk management (TPRM), also known as “vendor risk management,” is the management of risks introduced to your organization by its vendors, suppliers, contractors, and service providers. A third-party vendor is any outside party who plays an important role in your company’s ecosystem or supply chain.
Assume you have a close working relationship with a shipping agency who has access to all of your client information. You may have streamlined your logistics by allowing that agent access to your customer data, but you also created possible hazards from this third-party relationship (such as the agent accidentally disclosing your customer data online).
Why is Third Party Risk Management Important?
Many businesses now rely on third parties for a variety of services. It is also common for them to have access to secure networks and be responsible for storing confidential customer information. An attack on such a party can have significant consequences in this scenario.
Managing third-party risks is an increasingly important aspect of securing a business. Businesses should clearly understand who they work with, what risks they face, and how they can mitigate these risks.
- Firms Are Increasingly Reliant on Third-Parties: As outsourcing has become more accessible, many firms increasingly rely on third-party providers for everything from data storage to payroll. Most businesses would be unable to function properly if an important third party was attacked severely enough.
- Third-Party Security Varies Significantly: Third-party security practices differ greatly. Understanding whether parties constitute a risk to your firm often necessitates extensive research. Third party risk management guarantees that you understand each party’s security posture and replace them as needed.
- Third parties frequently gain access to your network: Third-party access to your network is frequently required. As a result, other parties are frequently given their own user credentials. If such credentials are stolen, the hacker will be able to get access to your network.
- You Are Liable for Third-Party Attacks: Third parties frequently keep confidential information; consequently, if the third party is hacked and that information is stolen, your company will be held liable. If your customer’s information is compromised, you are liable, even if the breach was caused by a third party. This not only jeopardizes your company’s reputation, but it may also lead to prosecution.
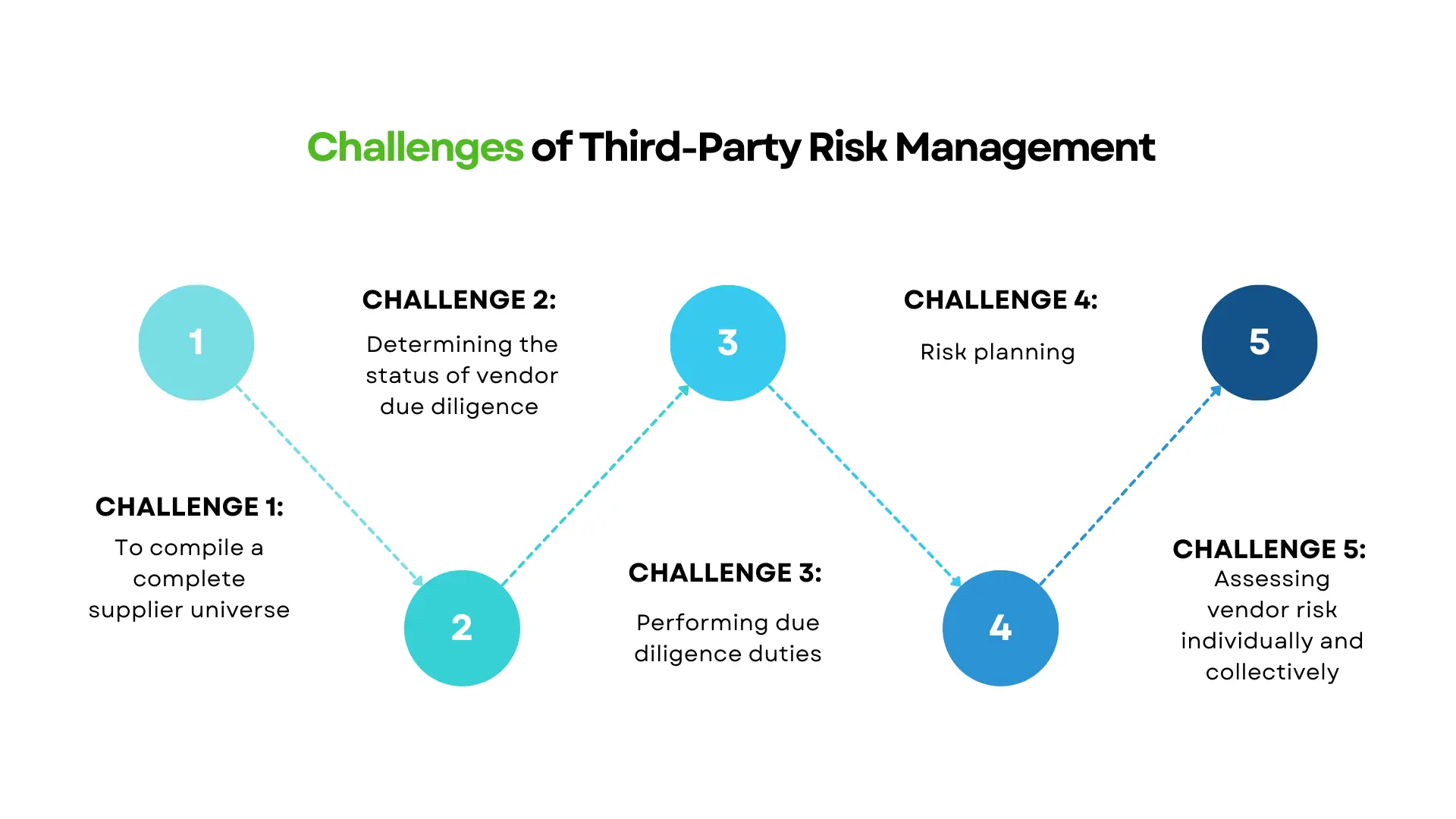
What are the Common Challenges of Third Party Risk Management?
Challenge 1: To compile a complete supplier universe.
The first difficulty in third party risk management is to provide visibility by developing and maintaining an inventory or register that covers the whole universe of current and prospective suppliers that may pose a risk to your organization. It is critical to remember that there may be more than one source of vendor information. Consider reconciling vendor information from many sources, such as compliance intake surveys, accounting financial spend, and legal contracts.
Challenge 2: Determining the status of vendor due diligence
The following difficulty is establishing and tracking the risk management activities required for each vendor at any given time. Organizations can apply multiple levels of due diligence operations for their vendors, which are generally aligned to a risk tier, based on a mix of criteria such as vendor type, criticality to the business, or risk level. Risk tiering enables organizations to determine the frequency of security reviews based on overall risk.
Challenge 3: Performing due diligence duties
Aside from maintaining the status of due diligence efforts, many organizations find it difficult to undertake a new vendor intake, send questionnaires, request vendor support, research, and then examine all material linked to that evaluation.
You can utilize survey tools or a service management/ticketing system to collect due diligence replies and documentation, but you will need to reconcile the data with your vendor universe. When you utilize an integrated vendor management solution, intake functionality, questionnaires, and communication features are frequently included, with replies entering directly into the vendor record. Remote or onsite audits of higher risk vendors may be required to guarantee compliance with organizational policies or alignment with stated risk tolerance.
Challenge 4: Risk planning
“Is the level of risk presented appropriate enough to move forward with this vendor, or are there mitigations that need to be addressed by the vendor, the internal business owner, or both?” The answer frequently hinges on the vendor’s risk category or the service’s importance in your business operations. When very few vendors have qualified, or none meet your security or privacy standards, a more severe difficulty arises. Some vendors will just not fulfill your organization’s requirements. Your organization may occasionally let a vendor correct a flaw or deviate from a policy that would otherwise exclude them from the partnership. When this happens, work with the vendor to set a realistic agreed-upon deadline.
Challenge 5: Assessing vendor risk individually and collectively
Completing the first four challenges is only one piece of the puzzle. The next challenge is combining all of this data to produce a picture of risk for a single vendor, specific organization or security threats impacted by a group of vendors, and an aggregate risk view of the supplier universe. When linking risks with vendors systematically, you can pivot the association to determine which risks are impacted by vendors. This knowledge may assist your organization in deciding which vendors to prefer, avoid, or even replace depending on risk rankings that ultimately aggregate to an overall TPRM risk. Transparent reporting to management on the riskiest third parties or business segments with the greatest levels of third-party risk can be beneficial.
How to Evaluate Third-Parties?
Evaluating third-parties is a critical component of an effective Third Party Risk Management. Here are some steps to evaluate third-parties:
- Identify the third party: The first step is to determine the nature and scope of the relationship with the third party. Understanding the type of service or product provided by the third-party, the level of access they have to sensitive data or systems, and the potential impact on the organization if the third-party fails to perform are all part of this.
- Due diligence: After identifying the third party, perform due diligence to obtain information on the third party’s financial soundness, reputation, and compliance with applicable laws and regulations. This can entail analyzing public documents, running background checks, and looking over the third-party’s qualifications and accreditations.
- Evaluate the third-party’s security posture: Determine whether the third-party has suitable security procedures in place to secure the organization’s sensitive data and systems. Conducting security assessments, reviewing security policies and procedures, and evaluating the third-party’s response to security issues are all examples of this.
- Examine the deal with the third party: Examine the third-party contract for suitable risk management terms, such as data protection, confidentiality, and indemnification agreements. The contract should also specify each party’s tasks and responsibilities, as well as provisions for termination, dispute resolution, and regulatory compliance.
- Monitor the third-party: After onboarding the third-party, keep an eye on their performance and compliance with contractual commitments, laws, and regulations. Conducting periodic audits, examining incident reports, and monitoring key performance indicators are all examples of this.
- Problems should be escalated: If issues are discovered throughout the evaluation or monitoring process, they should be escalated to the appropriate stakeholders, such as legal, compliance, or senior management, as needed.
How to Conduct a Third-Party Risk Assessment
Vendor risk evaluations can be time-consuming and burdensome, but the repercussions of failing to complete a good risk assessment can be excruciating. So, to do those assessments wisely, follow the methods outlined below.
Step 1: Recognize Your Vendor Risks
Begin by identifying all of the ways third-party partnerships can put your company at risk; not all of the categories described above will apply to every third-party relationship you have. Understanding all of the risks that may influence you allows you to evaluate providers more thoroughly.
Step 2: Establish Risk Criteria
You must now develop risk standards for third-party reviews after you have identified every potential risk category. These will differ based on the nature of the vendor’s and your company’s business. Create or apply a vendor risk assessment framework (one with a predetermined structure and grading requirements) to each review.
Step 3: Assess Each Good and Service
Two questions should be answered by a third-party risk assessment. How does this seller conduct business in general, and how does it handle the specific service or item you want to buy?
In terms of the company as a whole, ask questions like, “How might doing business with this party affect your company’s reputation?” Is the party adhering to legal and ethical business practises? How quick and dependable is its customer service? How financially secure is the company?
Step 4: Seek Professional Advice
When required, seek assistance from colleagues in other departments within your company or from other companies entirely. Seek assistance from compliance, financial, security, information technology, and legal authorities. Even better, you could construct a risk assessment team composed of a representative from each contributing department. This ensures accurate and timely estimates.
Step 5: Assess Each Vendor
Third-party risk assessments are employed in more than simply supply chains and vendor risk management software. You should research a vendor before forming a partnership with them, regardless of how little they are or what kind of goods or services they provide. Consider cleaning services, paper shredders, landscapers, landlords, and caterers even if you don’t conduct a formal risk assessment. They may pose a risk to your company if they gain access to your documents, data, and physical space.
Step 6: Arrange Vendors According to Risk Level
If you categorize potential vendors into distinct risk categories, you may make faster judgments about them and speed up the risk management planning process. First, assign a risk level to the vendor (high, medium, or low) based on your risk criteria. After that, assign a “business effect rating” to the seller. In other words, how important is the vendor’s product and service to your company? Determine the extent of due diligence you will undertake on vendors for each risk level. Bias is reduced while efficiency and consistency are increased by streamlining the approach.
Step 7: Develop a Risk Management Strategy
Create a customized risk management approach once you’ve agreed to work with a vendor and assess its level of risk. Plan how your organization will deal with or mitigate each potential risk that a third party may pose. When the threat strikes, you can then act quickly to minimize damage. The plan should include risk scenarios and specific reaction obligations, as well as the name or function of the person in charge of each.
Step 8: Stay Current on Regulations
Your company must be kept up to date on new and changed rules and regulations. These regulations include, but are not limited to:
- Privacy laws and regulations
- Environmental restrictions
- Employment and labor legislation
- Tax legislation
As you alter your own rules and procedures to keep up with changing regulatory expectations, evaluate all of your vendors to ensure they can retain compliance. If a vendor is unwilling to modernize its processes, you may be held liable for that vendor’s failure to comply with regulations.
Step 9: Finish Annual Evaluations
Vendors evolve and adapt in the same way that your company does. As a result, their practices may be out of sync with your requirements or expectations. Depending on the level of risk, you can analyze a vendor on a monthly or annual basis. Continuous monitoring and due diligence ensure that your business relationships are safe and beneficial for all parties.
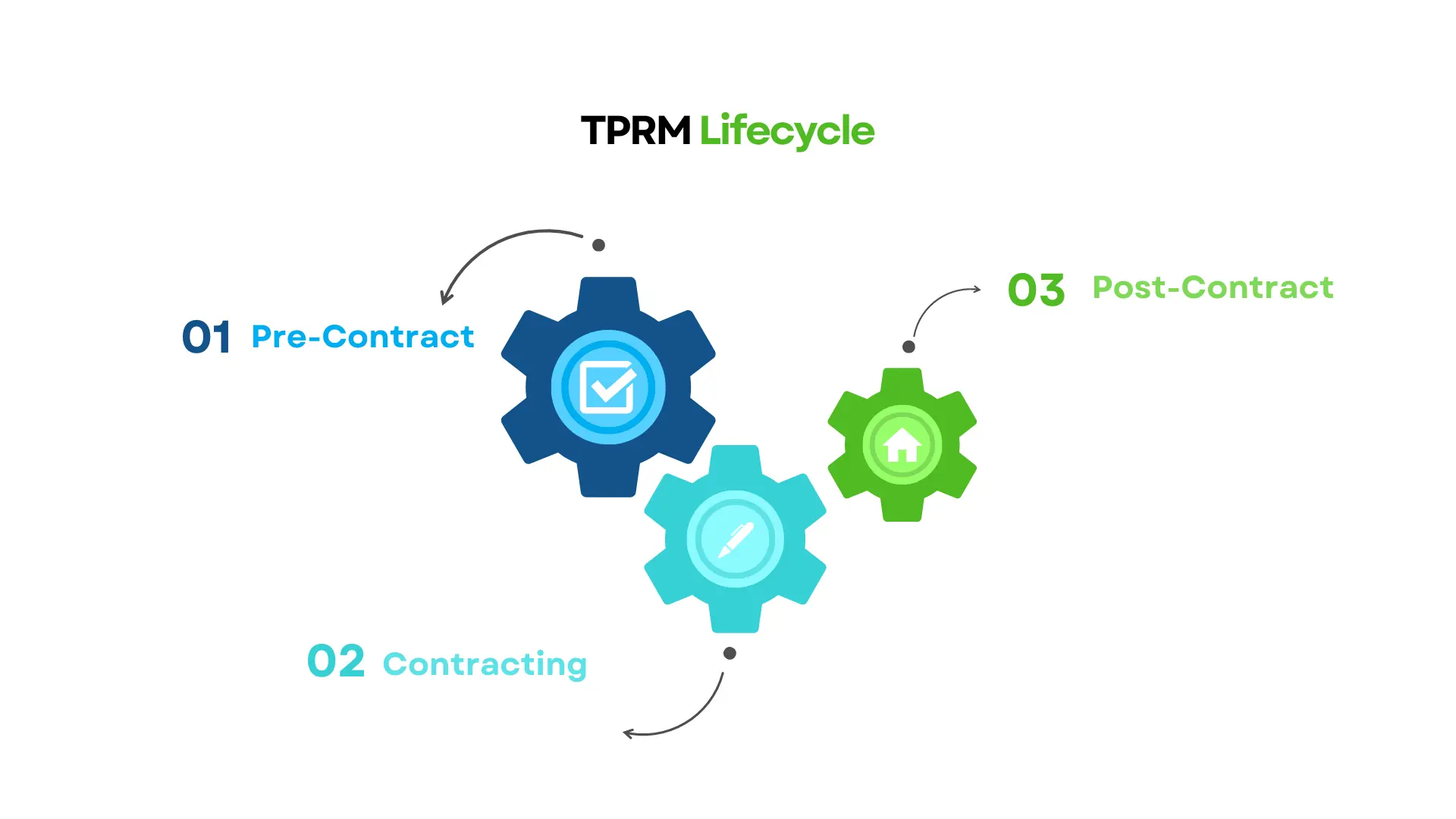
What is the Third Party Risk Management Lifecycle?
The third party risk management lifecycle is a crucial framework for organizations to identify, assess, mitigate, and monitor risks associated with third-party vendors, suppliers, and service providers. As companies increasingly rely on outsourced services, cloud solutions, and supply chain partners, managing third-party risks has become essential for data security, regulatory compliance, operational efficiency, and reputation management.
A third-party vendor relationship progresses through three key stages:
Pre-Contract: Risk Assessment & Due Diligence
Pre-contract risk management begins before you sign a contract with a third-party vendor. Following the identification of new third-party providers, you must conduct a third-party risk assessment to determine the inherent risk and criticality. You must consider the categories of information handled by each third-party vendor, as well as the potential financial, reputational, and legal consequences of a data breach.
It is crucial to identify these inherent third-party risks because you will use this information to conduct risk-based due diligence on them. This is also an important phase in the risk management process since it allows you to delve further into the rules, procedures, and controls of the third-party vendor. The vendor is needed to complete the questionnaire and provide pertinent evidence for each control.
Contracting: Risk Allocation & Compliance Assurance
If the dangers can be reduced, it’s time to negotiate contract terms and start working with a vetted third-party provider. You must establish sound contracting concepts and provisions. It is critical to determine which risks are being accepted by the parties and to achieve the proper risk distribution balance.
You should not rush through contracting since a robust contract is crucial for managing third-party risk. As you begin working with a third party, you should keep reviewing the contract to ensure that the vendor is achieving your expectations and service level agreements.
Post-Contract: Ongoing Risk Monitoring & Vendor Management
Post-contract monitoring is the final stage of the third party risk management lifecycle, which begins after the contract is signed. This stage is sometimes overlooked, but it is where the actual danger begins. The following four important activities should be included in the post-contract monitoring process:
- Continuous monitoring helps you to keep an up-to-date perspective of third-party risks that may arise as a result of changes in credit ratings, new lawsuits, large layoffs, or other events that may affect their overall risk posture.
- Point-in-time monitoring enables you to examine risks on a regular basis by administering surveys and reviewing documents such as SOC reports, information security policies, and financial statements.
- Risk assessments are undertaken on a regular basis as third-party partnerships expand and evolve to identify what has changed and whether extra diligence or contract revisions are required.
- Structured third-party offboarding is based on your exit strategy and assists in de-risking third-party contracts and relationships. It comprises operations like returning or destroying data, removing system access, ensuring the completeness and accuracy of all deliverables, etc.
What is a Third Party Risk Management Framework?
TPRM frameworks offer organizations a road map for developing third party risk management programmes based on industry best practices. Frameworks can be utilized to establish a TPRM programme and to provide baseline control requirements to third-party vendors and suppliers.
There are two types of third party risk management frameworks namely Shared Assessments TPRM Framework and NIST 800-161. These two frameworks are used for building a TPRM or supply chain risk management (SCRM) programme. Then there are ancillary information security frameworks, such as NIST CSF v1.1, ISO 27001, and ISO 27036, that can augment a TPRM programme or assist in the creation of vendor risk assessment questionnaires.
How Do I Select a Third Party Risk Management Framework?
Your organization’s legislative requirements, acceptable level of risk, use of third-parties, business processes, joint ventures, compliance requirements, and overall enterprise risk management strategy should all influence your choice of a third party risk management framework. Organizations are now directly utilizing third-parties in their supply chain, as well as ancillary services such as sales, distribution, and support. The growing use of technology, such as the cloud and cloud-based apps, is hastening the trend towards outsourcing and raising the dangers connected with it.
Furthermore, the importance of the jobs performed by third-party vendors is increasing, increasing the impact of third-party vendor disruption or failure. In many firms, particularly those operating in regulated contexts, third-party risk is a feature on board agendas with CEO/board-level accountability. As organizations become more decentralized, the requirement for consistent third-party governance systems grows. Best-in-class organizations make considerable use of third-party resources while effectively managing the risks connected with them.
10 Best Practices in Third Party Risk Management
1. Create a distinct and engaging vision. A vision will guide you through the setup process and is essential for management buy-in.
2. Involve internal stakeholders early in the design and implementation of third party risk management, such as risk and compliance, security, procurement, and commercial actors.
3. Think about a centralized third party risk management architecture that allows for risk assessment on behalf of and with input from the business. A centralized model promotes standardization and is frequently less expensive.
4. Make certain that the mandate for third party risk management is adequately stated in the relevant policy and procedures.
5. Make use of specialized third party risk management tools. Use specialized TPRM software.
6. Make a distinction between third parties and contracts. It is recommended to build a third-party inventory (i.e. a third-party catalog) as well as one of the contracts.
7. Assign a risk profile to each of your third-party vendors and contracts. You may select what to analyze and in what order by prioritizing your third parties and contracts. This is especially beneficial if you have a large number of providers.
8. Base your due diligence judgment on the risk profile, service type, contract value, and other factors.
9. Match the duration of the review to the risk profile of your third parties and contracts. In a nutshell, you should test critical vendors more frequently than non-critical ones.
10. Before you submit the first due diligence assessments, start thinking about the data collecting, processing, and tracking process. Again, specialized tools can be useful for securely processing the assessment findings, performing a first analysis of the responses supplied, and initiating follow-up.
Frequently Asked Questions
Who is responsible for third party risk management?
Third party risk management (TPRM) is a collaborative effort involving executive management, risk management teams, business unit leaders, procurement and vendor management teams, legal and compliance departments, and IT and cybersecurity teams. Together, they work to assess, monitor, and mitigate third-party risks effectively within the organization.
What does third party risk management mean in procurement?
In procurement, Third Party Risk Management (TPRM) refers to the process of identifying, assessing, and mitigating risks associated with engaging third-party vendors, suppliers, or service providers.
This includes evaluating their financial stability, operational capabilities, regulatory compliance, and cybersecurity posture, among other aspects. The goal is to ensure that procurement decisions align with the organization’s risk management objectives and minimize potential negative impacts on the business due to third-party relationships.
What is a TPRM tool?
A third party risk management tool is a software solution designed to help organizations to streamline and automate the process of identifying, assessing, and managing risks associated with third-party relationships. These tools typically offer features such as risk assessments, due diligence, ongoing monitoring, and reporting to help organizations effectively manage third-party risks.